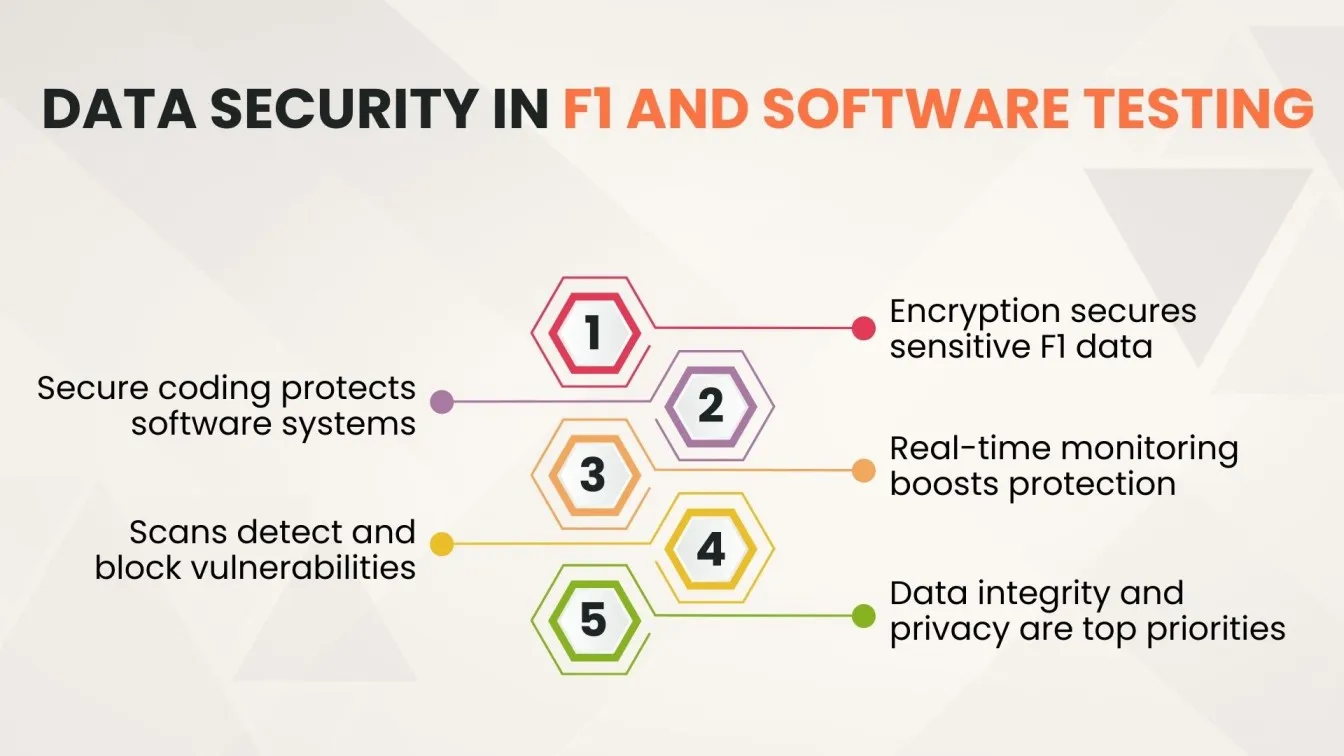
Safeguarding sensitive data is a top priority, especially in high-stakes environments like Formula 1, where real-time telemetry and strategic information must be protected against unauthorized access. F1 teams depend on robust data security solutions to maintain the integrity and confidentiality of their digital assets. Similarly, software testing security standards emphasize rigorous security testing practices, such as application security testing, penetration testing, and compliance with standards like ISO/IEC 27001. Both domains highlight the critical importance of comprehensive security measures to prevent data breaches and ensure seamless, secure operations.
What’s next? Keep scrolling to find out:
🚀 Master Security Testing: Learn essential security and penetration testing techniques.
🚀 Upgrade Data Protection: Use advanced tools for data security and privacy.
🚀 Automate for Speed: Apply smart automation for efficient software testing.
🚀 Secure Access & Detect Threats: Set up strong access control and AI-driven threat detection.
🚀 Think Like F1: Adopt F1’s speed and precision in your testing strategy.
Introduction to F1 Data Security and Software Testing Practices
Formula 1 (F1) and software development both prioritize robust data security and rigorous security testing to protect sensitive information. Implementing advanced data security solutions and data protection measures ensures this information remains confidential and protected from cyber threats. Similarly, in software development, security testing - including application security testing, penetration testing in cybersecurity, and automation software testing- is essential to identify and mitigate vulnerabilities, ensuring data security and privacy. Both fields employ comprehensive security testing services and data protection solutions to maintain the integrity and confidentiality of their critical data.
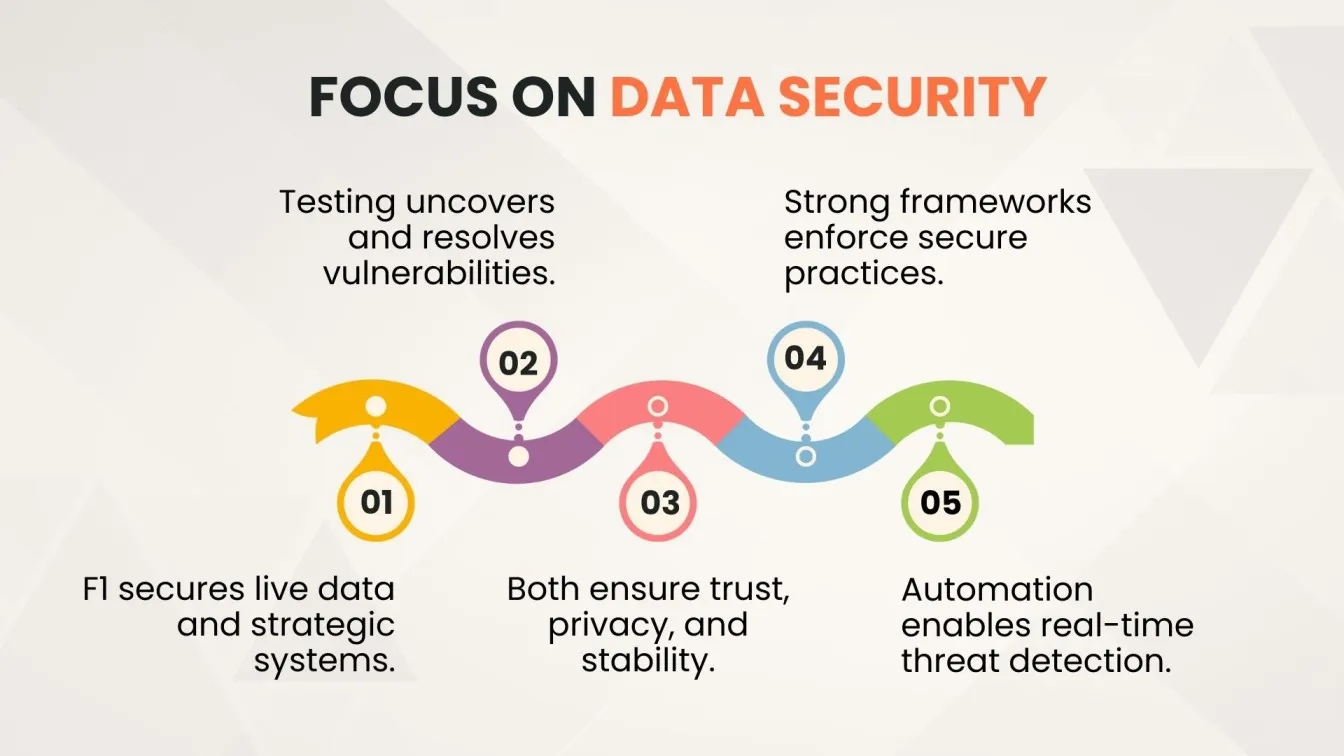
Why Data Security Is Critical in Formula 1
Formula 1 produces vast amounts of critical data every second, making robust data security essential for protecting performance metrics and strategic decisions.
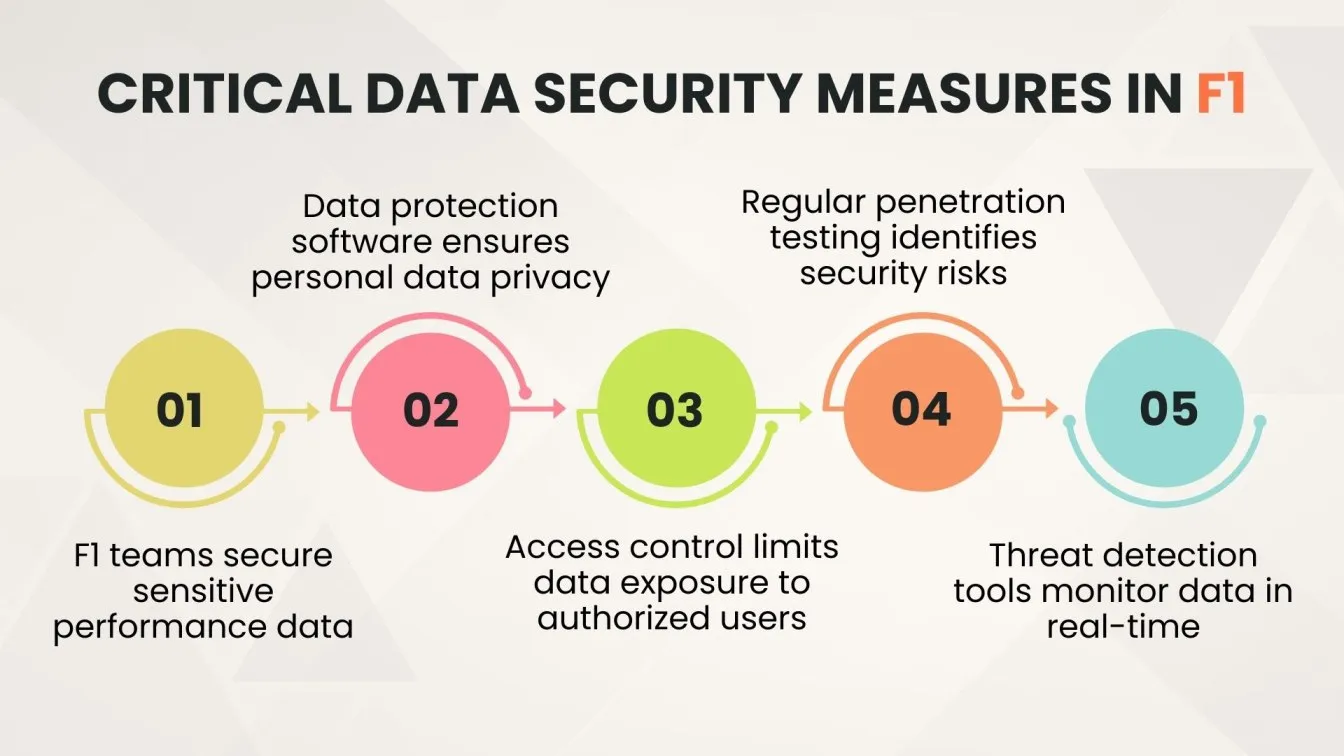
- Data Protection & Privacy:
F1 teams use data protection software, data protection solutions, and comply with the General Data Protection Regulation to secure personal data protection and internal strategies. - Preventing Breaches:
F1 teams rely on data security software, advanced data protection, and robust access control systems to safeguard against leaks. - Access Control & Security:
Implementing access control security and role-based access control ensures that only authorized personnel can access mission-critical data. - Security Testing & Monitoring:
Regular cybersecurity penetration testing, application security testing, and threat detection tools are used to identify risks early.
Overview of Secure Software Testing in Modern Development
From early code reviews to final deployment, applying robust software testing services ensures vulnerabilities are caught before attackers can exploit them.

Core Components of Secure Testing:
- Application security testing and security testing services are vital for identifying gaps.
- Automation testing speeds up processes and reduces human error in testing software.
- Tools for security testing, security penetration testing, and cybersecurity penetration testing simulate attacks to harden systems.
- Access control systems, including role-based access control and network access control, are verified to restrict unwanted access.
Strategic Importance:
- Prevents social security data breach incidents.
- Integrates data protection software, advanced data protection, and complies with the General Data Protection Regulation.
- Uses threat detection tools like AI threat detection to monitor in real time.
Key Technologies Behind F1’s Data Protection Systems
In Formula 1 testing, safeguarding sensitive information is paramount. Teams employ a suite of advanced technologies to ensure robust data security and privacy:
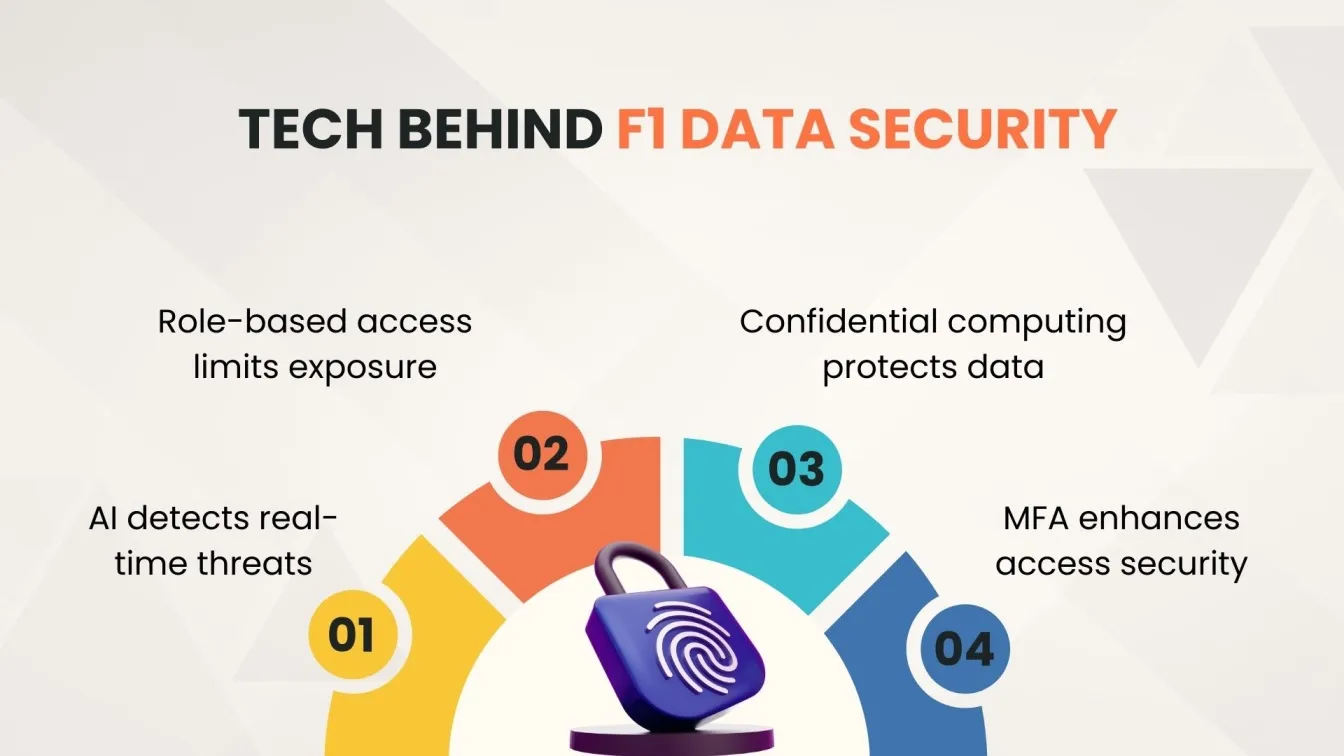
- AI-Powered Threat Detection Tools: Utilizing artificial intelligence, these systems continuously monitor network activity to identify and neutralize potential cyber threats in real-time, enhancing overall security posture.
- Role-Based Access Control Systems: Implementing role-based access control ensures that only individuals access the data necessary for their roles, minimizing the risk of unauthorized data exposure.
- Confidential Computing: This technology protects data during processing by performing computations in a hardware-based trusted execution environment, safeguarding against unauthorized access or modification during computation.
- Multi-Factor Authentication (MFA): This approach significantly reduces the risk of unauthorized access, even if one authentication factor is compromised.
Understanding Vulnerabilities in Software Without Secure Testing
Skipping security testing in software testing environments can leave applications exposed to hidden vulnerabilities, endangering user data and overall system security.

- Injection Flaws: Absence of security penetration testing can leave systems susceptible to attacks like SQL injection, where malicious input compromises backend databases.
- Broken Authentication: Without penetration testing in cybersecurity, flaws in authentication mechanisms may persist, allowing unauthorized access to sensitive information.
- Insecure Dependencies: Failing to employ software testing services to scrutinize third-party components can introduce vulnerabilities, as these dependencies might harbor exploitable flaws.
- Data Exposure: Lack of data security solutions can result in inadequate protection of sensitive data, leading to potential breaches and loss of personal information.
Real-Time Data Handling in F1 vs. Application Data Flow in Software Testing
Real-time data handling plays a critical role in F1’s testing platform and Software Engineering practices by ensuring data flows securely and efficiently across systems.
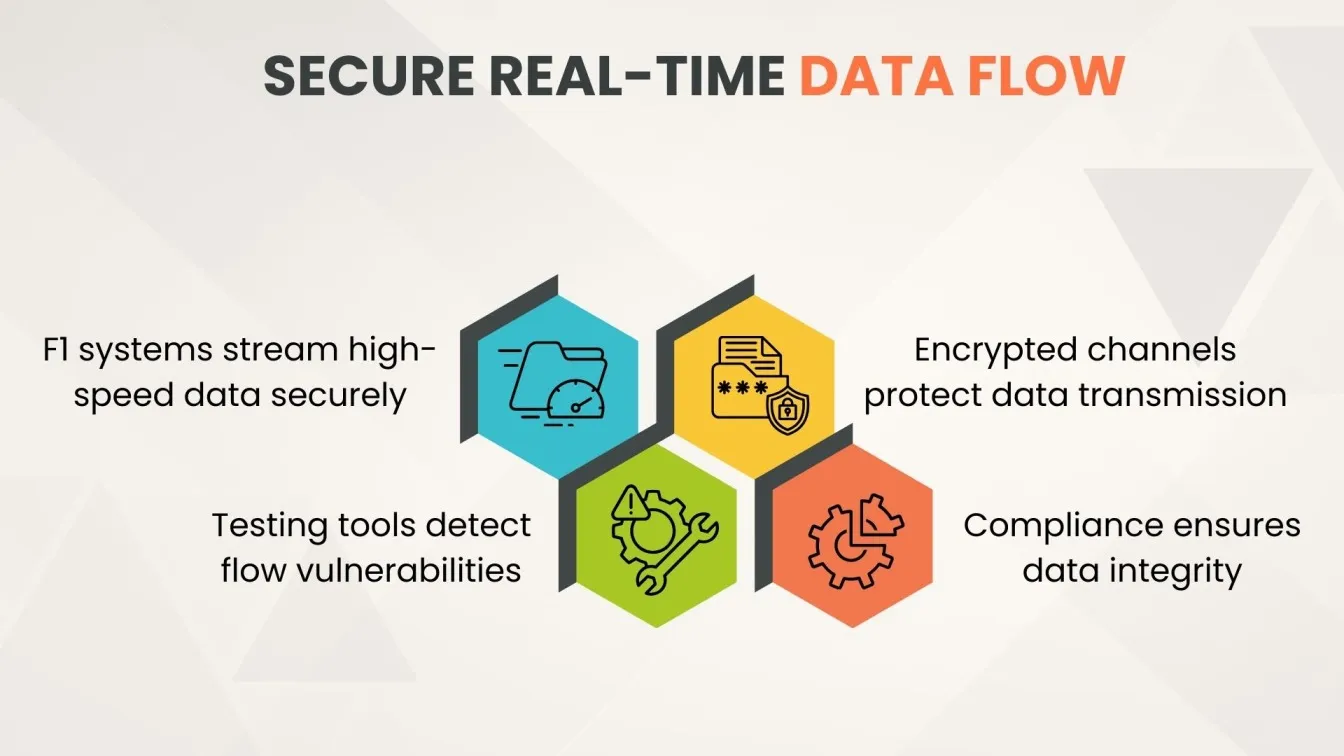
F1 - Real Time Data Handling
- Telemetry Systems: F1 testing tools collect high-speed data to detect abnormal activity and potential vulnerabilities in real time.
- Secure Transmission: Data is sent via protected networks, using strong security protocols to prevent potential security threats and ensure compliance with security standards.
Application Data Flow in Testing
- Data Flow Testing: In Software Engineering, it helps uncover risks in traditional systems, such as uninitialized variables and insecure transitions.
- Security & Compliance: Analysis tools play a critical role in flagging compliance issues, blocking potential security threats, and securing application workflows.
Comparing Threat Detection in F1 and Secure Software Testing Tools
Both Formula 1 testing and software testing rely on advanced threat detection tools to ensure peak performance and strong data security.
Encryption Standards in F1 vs. Web and App Testing
Effective data security relies heavily on strong encryption standards, whether in the high-speed environment of Formula 1 testing or modern software testing frameworks.
F1 Telemetry Encryption:
In Formula 1 testing, real-time data, to prevent leaks and maintain strict security policies, teams use AES (Advanced Encryption Standard). This method safeguards strategic data against interception, meeting compliance demands while addressing security concerns unique to the environment. With telemetry being a critical component, robust encryption ensures every byte of data remains confidential.
Web & Application Encryption:
In web and app testing, TLS (Transport Layer Security) encrypts communication between users and servers. It protects common types of sensitive data, like login credentials and user inputs, during transmission. Security experts use penetration testing and data protection software to ensure resilience against cyber threats. Integration with cloud infrastructure and use of machine learning systems further strengthens defenses, identifying anomalies and adapting to evolving attack vectors.
Role of Automation in F1 Security and Software Testing Environments
Automation plays a critical role in both F1 security platforms and software testing, ensuring faster threat detection, real-time monitoring, and strong data protection.
In F1 Security:
- F1 teams use automation testing tools to simulate stress scenarios and monitor systems for abnormal activity during live events.
- AI-based threat detection systems analyze telemetry data in real time to spot anomalies or potential security threats, helping prevent failure.
- Automated systems also enforce compliance, data encryption, and access controls, meeting high data security standards.
In Software Testing:
- Automation testing boosts development speed while maintaining secure, high-quality code.
- It enables cybersecurity testing, application security analysis, and penetration testing with minimal manual work.
- Combined with data protection tools and access control systems, automation helps identify potential vulnerabilities and ensures secure deployments.
Incident Response: F1 Protocols vs. Software Security Testing Workflows
Effective incident response plays a crucial role in both Formula 1 testing and software security testing workflows, though their execution differs due to real-time vs. structured environments.
F1 Incident Response:
- Real-Time Monitoring: F1 platforms use sensors and AI to stream telemetry data (e.g., system load, fault patterns) for quick detection of abnormal activity, potential risks, security flaws, potential security threats, or compliance violations.
- Immediate Action: Automated systems or teams act instantly, adjusting operations, isolating affected modules, or rerouting processes to protect critical systems, safety-related systems, and maintain data integrity.
Software Security Testing Workflows:
- Structured Processes: Security teams follow fixed steps - preparation, detection, containment, eradication, recovery, and lessons learned during security testing or penetration testing in cybersecurity.
- Detection and Analysis: Tools like application security testing tools and threat detection software identify common vulnerabilities, unauthorised access, or malicious activities.
- Containment and Eradication: Threats are isolated and resolved using security testing services and code security analysis tools.
- Recovery and Review: Systems are restored with minimal impact to production environments and business operations, improving future defenses through vulnerability assessment and review.
How F1’s Speed and Precision Influence Security Measures
In Formula 1 testing, speed and precision are not just performance benchmarks, they also drive for the cybersecurity environment. Protecting this information requires data security solutions and application security controls capable of operating in real time.
Formula 1 makes any security risks or data breach a potential threat to both safety and competitiveness. To counteract malicious attacks and unauthorised access, teams partner with security experts and use a combination of security tools, like threat detection tools and code security analysis tools, to ensure performance remains unaffected.
Precision is also key in cybersecurity. F1 relies on real-time monitoring, access control systems, and vulnerability assessment to identify potential security threats instantly. Ultimately, the blend of speed and precision in F1 pushes the evolution of data security, network security, and secure coding practices, reinforcing how application security testing plays a critical role in protecting sensitive systems in high-stakes environments.
Best Practices Shared Between F1 Data Security and Secure Testing
In both Formula 1 data security and secure software testing, several best practices are shared to ensure the protection of sensitive information and maintain system integrity. Key practices include:

1.Early Integration of Security Measures:
- F1: Security protocols are embedded from the beginning to reduce the attack surface and address vulnerabilities proactively.
- Testing: Security testing is integrated early in development to detect and fix issues before they evolve into major security incidents.
2.Regular Assessments:
- F1: Continuous assessments and audits are performed to ensure compliance, monitor network security, and safeguard the platform.
- Testing: Regular vulnerability scans and penetration testing help strengthen defenses and reduce the risk of exploitation.
3.Encryption and Access Control:
- F1: All data is encrypted, and strict access controls limit entry to authorized users, reducing the chances of network security breaches.
- Testing: Encryption and role-based access policies protect test data and minimize the exposure of critical information.
4.Incident Response:
- F1: A robust incident response plan ensures quick actions during security incidents, minimizing disruption and data loss.
- Testing: Teams follow well-defined strategies to address incidents swiftly and restore secure operations with minimal impact.
Lessons Software Testers Can Learn from F1’s Approach to Data Protection
Software testers can take a page from the F1 playbook to reinforce data protection and security testing in their workflows. Here are a few key lessons:

- Enforce Access Control Security
Use robust role-based access control and network access control systems to limit unauthorized access, just as F1 teams restrict access to sensitive car telemetry and race strategy data. - Invest in Threat Detection Tools
F1 teams rely on advanced persistent threat detection and AI threat detection tools. Similarly, testers should utilize threat detection software to proactively identify vulnerabilities in applications. - Apply Data Masking & Personal Data Protection
F1 handles confidential data through masking techniques. In testing software, use data protection software and personal data protection strategies to comply with the General Data Protection Regulation (GDPR). - Conduct Cyber Security Penetration Testing
F1 environments are frequently tested for intrusions. Adopt penetration testing in cybersecurity and application security testing to mimic real-world attacks in your software.
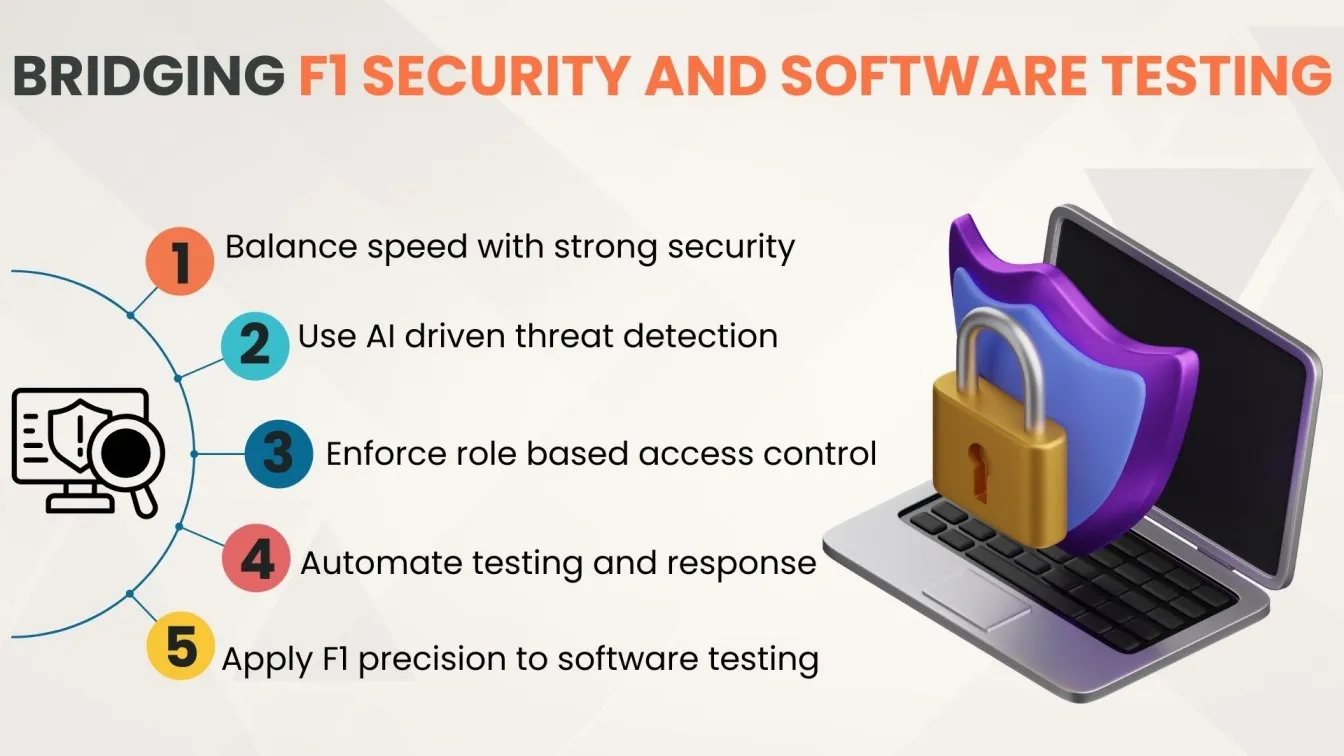
Conclusion: Bridging the Gap Between F1 Security and Software Testing
In both Formula 1 and software development, the demand for speed must never compromise data security and data protection. While F1 engineers rely on cutting-edge data security solutions, access control systems, and threat detection tools to protect real-time telemetry and race data, software testers must adopt similar standards through automation testing, penetration testing in cybersecurity, and robust security testing services.
By learning from the precision and discipline of F1 protocols, software professionals can enhance application security testing, ensure better personal data protection, and implement more advanced data protection solutions. Whether it's AI threat detection or role-based access control, the fusion of F1 security practices with modern software testing services ensures a stronger, more resilient digital future.
Frugal Testing Company offers comprehensive functional testing services to ensure the reliability and performance of software applications. As a trusted software testing service provider, they specialize in delivering high-quality testing solutions that cater to diverse business needs. Their AI-driven test automation services accelerate the testing process, providing faster and more accurate results. With expertise in various domains, Frugal Testing ensures that applications are thoroughly tested for performance, security, and functionality. Explore the range of services offered by Frugal Testing to enhance your software's quality, minimize risks, and improve user experience.
People Also Ask
How is third-party vendor security ensured?
Third-party vendor security is ensured through due diligence, risk assessments, compliance audits, and the implementation of strict access controls and SLAs.
What are the three components of the security management process?
The three key components are risk assessment, security policies and procedures, and incident response planning.
What role does encryption play in F1’s data security protocols?
F1 teams use encryption to secure data during transmission, preventing unauthorized access and ensuring data integrity.
How is rapid data access securely managed?
It is managed through role-based access control (RBAC), multi-factor authentication (MFA), and encrypted storage and transmission.
What is the difference between a security incident and a data breach?
A security incident is any event that threatens security, while a data breach specifically involves unauthorized access to sensitive data.




%201.webp)