Amazon Web Services is one of the most popular cloud service providers globally, and every major company uses it to develop and deploy cloud infrastructure on AWS. When building cloud applications, security is highly important as one wrong step can expose your important data to the open internet. Hence, penetration testing is important.
In this article, we will explore the importance of penetration testing, AWS’s shared responsibility model, and a step-by-step guide to AWS penetration testing.
So, let’s first start by understanding the importance of penetration testing.
Importance of Penetration Testing

1. Compliance Requirements
Many organizations deal with sensitive data points, and they are subject to HIPAA, PCI, DSS, GDPR, and many other compliance and regulatory laws. Penetration testing is important to becoming compliant with such laws. It also helps identify non-compliant AWS resources. If any resource is non-compliant, the organization may face lawsuits and reputational damage, too.
2. Fulfilling Client Responsibilities
AWS follows a shared responsibility model, where the client is also responsible for securing resources and data on AWS. Every user must comply with the shared responsibility model and fulfill their responsibilities of securing their resources. By penetration testing on AWS, clients can verify that their resources, data, and other AWS workloads are secure and only accessible to them with valid credentials. Doing such testing also reduces the chances of data breaches or unnecessary exposure to computing resources.
3. Security Assurance
When deploying apps on the cloud and serving lots of users across the globe, many organizations are unsure about their security posture, and this can cause serious concerns over the security of data and resources. By penetration testing, organizations can verify that their apps are secure and they cannot be accessed outside the AWS environments without proper access. Moreover, penetration testing offers security assurance and peace of mind as the users know that everything is well-tested and secured.
Knowing the importance of penetration testing in AWS, you might think that you can penetration test everything in AWS, and it is your responsibility to keep everything secure. But that’s not correct. In the next section, we will discuss the AWS shared responsibility model, which can clear such doubts.
AWS Shared Responsibility Model
AWS follows a shared responsibility model while serving its clients across the globe. As the name suggests, no single party is completely responsible for infrastructure security in the cloud; rather, both parties come together and focus on different elements to keep the cloud secure. AWS breaks down cloud security into two different segments, as shown below.
- Security In the Cloud
Security in the cloud is the segment associated with the resources deployed by any client. In this security segment, clients are fully responsible for configuring their resources correctly, restricting access to them through access control measures, and regularly patching or updating them to keep them secure from any vulnerabilities. As an AWS customer, you can perform penetration testing to verify your infrastructure setup under this part.
- Security of the Cloud
Security of the cloud is the segment associated with securing the AWS platform and its physical locations. AWS and its engineers are completely responsible for providing this security to customers across the globe. You cannot perform penetration testing of physical locations or the AWS cloud platform. If there are any vulnerabilities, it is AWS’s responsibility to fix them and provide a safe experience to customers.
By now, you know the importance of penetration testing and also understand the AWS shared responsibility model perfectly. So, this is the right time to learn the step-by-step guide to AWS penetration testing for your cloud resources.
Step-by-Step Guide to AWS Penetration Testing
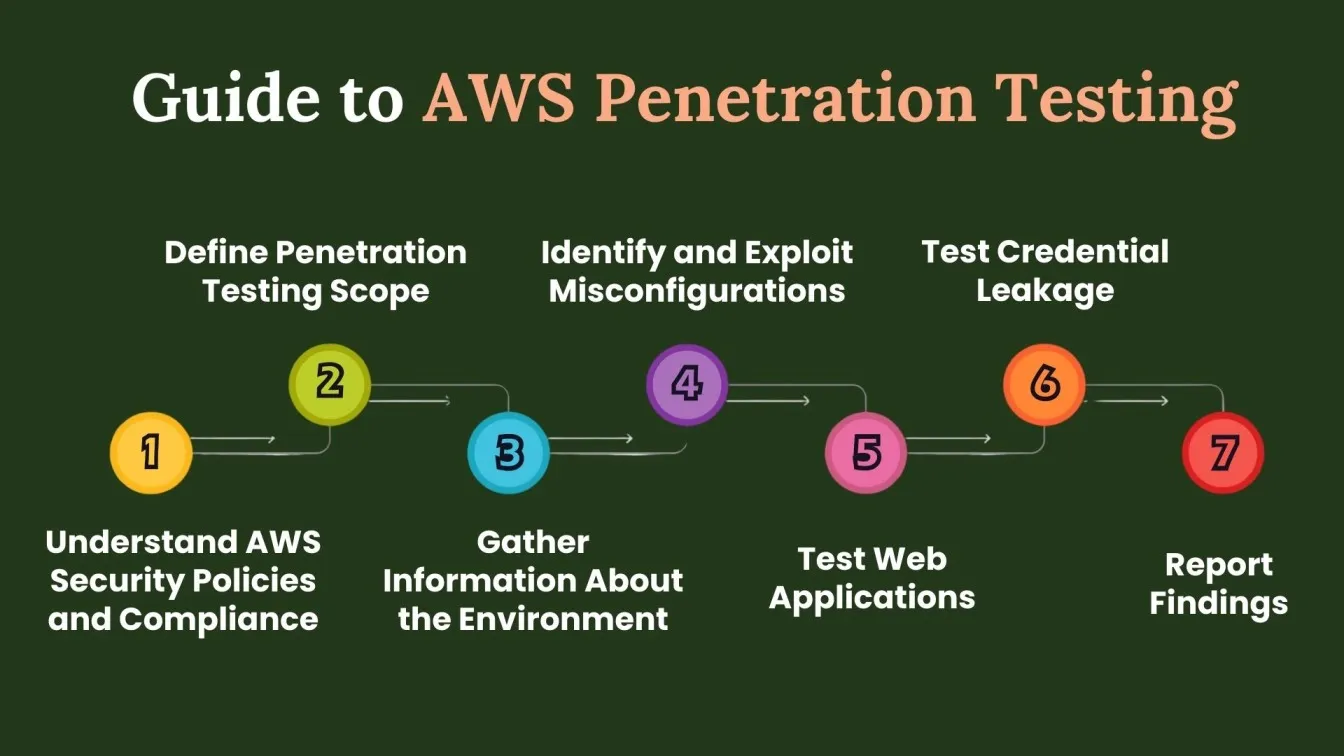
- Understand AWS Security Policies and Compliance
Before you start planning for your AWS penetration testing project, it is better to understand the security policies and compliance of AWS. Understand the shared responsibility model to find areas that you can test and avoid the ones that you cannot test.
Moreover, you should also check out AWS’s penetration testing guidelines and how each service should be tested to do penetration testing of your resources in the correct way. Lastly, if your penetration testing project requires special requests, you should get approvals from AWS by submitting a penetration testing request explaining your testing scenarios and the approvals you require.
- Define Penetration Testing Scope
After understanding the penetration testing guidelines, you should define the scope of your testing. By defining scope, you can create a boundary for your test cases and limit your test cases to relevant areas only.
When creating the scope of your penetration testing projects, you should also get the scope approved by other testers and relevant stakeholders. This will ensure that you are testing the correct things and have approvals for your penetration tests.
- Gather Information About the Environment
Once your testing scope is defined, it is time to gather information about the environment you wish to test. AWS provides many services, and there are different ways to test each service.
At this stage, you should understand the basics of each service you wish to test, find ways to perform penetration testing on the defined resources and create a list of test cases that you wish to perform during the testing project.
- Identify and Exploit Misconfigurations
Misconfigurations are one of the biggest issues in cloud security, and it is important that you identify, exploit, and report them before anyone else. Common misconfigurations include basic passwords, publicly accessible S3 buckets, overly permissive IAM roles or policies, unsecured API gateway endpoints, etc.
You can use various network testing tools to exploit misconfigurations and report them actively in your penetration testing reports.
- Test Web Applications
After exploiting common misconfigurations in AWS environments, it is time to test web applications hosted in AWS services and servers. You should test API gateways, lambda functions, EC2, or containers hosted in AWS to find and exploit vulnerabilities.
To test web applications, you can use tools like Burp Suite, OWASP, ZAP, etc. During this testing stage, you should also explore server-side misconfigurations with services like Cloudfront, S3, and WAF.
- Test Credential Leakage
Credential leakage is a big security issue for many organizations, which can also lead to getting your resources hacked by malicious hackers. In this penetration testing step, you should search through the logs of all of your resources and look for any log lines that include credentials or any secret keys associated with your resources.
- Report Findings
The last step in penetration testing your AWS resources is to create a comprehensive report of your findings, which includes ways to reproduce the security errors and suggestions for changes to fix such errors. Having a better report outlining all the penetration testing test cases makes it easier to verify the crucial cloud computing challenges whenever they are fixed.
Final Words
Coming to an end, penetration testing is not easy, but it is important that you don’t miss this. Doing deep penetration testing of your AWS resources can save you and your cloud resources from being compromised and used by malicious hackers. Follow the step-by-step guide discussed here, and you can verify your cloud infrastructure's security easily.




%201.webp)