Are you interested in security testing but confused by the technical terminology? We'll simplify everything for you.
We have been working on the best security testing practices since 2016 and this guide is worth checking out -
📌Learn the benefits and drawbacks of security testing and discover why it is so important to face Security risks.
📌Gain an understanding of the fundamental security testing frameworks; we shall talk about them later.
📌Discover some quick suggestions for effective security testing using our recommended procedures.
📌Use our best practices to learn about the ways to tackle the newest security testing challenges.
📌Find out what 2024's newest security technologies are including expertise opinions for testing on mobile, the web, and APIs.
📌Effective security testing is essential for software security to guard against threats and vulnerabilities.
As we explore a little bit of security testing. Let's explore the ins and outs of security testing and let's see why security testing plays an important role.
.webp)
What is Security testing?
📢Security testing evaluates when software is susceptible to cyberattacks and evaluates how unexpected or malicious inputs affect the program's functionality.
📢Finding any potential weaknesses or vulnerabilities in the software system that could allow employees or outsiders to steal data, money, or reputation is the aim of security testing.
📢It additionally helps in the detection of any potential security threats in the system and supports developers in using code to solve issues.
📢It is the process of integrating security testing tasks throughout the numerous stages of the software development life cycle (SDLC), such as planning, designing, developing, testing, deploying, and maintaining the product.
📢An essential component of guaranteeing the dependability and integrity of apps that use APIs (Application Programming Interfaces) is API security testing
.webp)
Why Is Security Testing Important?
📢For a number of reasons, security testing is essential while developing and maintaining software applications.
🟡Protecting Confidential Information: Security testing assists in locating weaknesses that might allow for illegal access, data breaches, or the disclosure of private data.
🟡reventing Unauthorized Access: Security testing assists in locating and fixing holes in authorization and authentication systems.
🟡Compliance with Regulations: Security testing assists companies in making sure that their applications adhere to these rules in order to prevent fines and other legal repercussions.
🟡Mitigating Financial Loss: A security breach may cause large financial losses for a number of reasons, including the expense of resolving the breach, legal bills, harm to one's reputation, and missed business possibilities.
🟡Maintaining Reputation and Trust: Users expect firms to focus on security because they trust them with their data. An organization's reputation can be severely damaged by security breaches, which can result in a loss of trust from stakeholders, partners, and customers.
🟡Preventing Disruption of Services: Security flaws can be used to interfere with an application's or system's regular operation.
🟡Staying Ahead of Evolving Threats: New security vulnerabilities are frequently discovered, and cyber threats are always changing and it is important to protect the development teams source code.
💁As an outcome, we now know a little bit more about researching the specifics of security testing. Let's now discuss several software security testing application features and frameworks that are likely to be helpful in 2024.
.webp)
Must Try Security Testing Frameworks: Things to Know in 2024
💁One of the greatest methods for preventing and analyzing network and application layer attacks is to use software security testing tools. The goal of network security testing tools is to prevent cyberattacks at the network level and illegal access.
⏩ OWASP ZAP (Zed Attack Proxy): During the development and testing periods of web application development, this open-source security testing tool can be used to identify security vulnerabilities.
Example: ZAP proxy.
⏩Burp Suite: A well-liked tool for web application security testing is Burp Suite. It provides a number of tools for the penetration testers and security experts.
Example: Proxy, Intruder, Repeater, Web application scanner.
⏩Metasploit Framework: A penetration testing framework called Metasploit aids in finding and taking advantage of vulnerabilities. It contains a vast assortment of payloads, exploits, and penetration testing tools.
Example: Exploitation modules, Payloads, Post-exploitation modules, and Auxiliary modules.
⏩Nmap (Network Mapper): Nmap is a potent network scanning utility that can be used to find hosts and services on a computer network, even though it isn't strictly a security testing framework. It is commonly used in security assessments to identify open ports and potential security vulnerabilities.
Example: Host discovery, Port scanning, Version detection,
⏩Wfuzz: Wfuzz is a web application security testing tool that focuses on brute force and fuzzing techniques to discover security vulnerabilities.
Example: Customizable fuzzing, support for multiple protocols (HTTP, HTTPS, FTP, etc.)
⏩Wireshark: A network protocol analyser that is often used. It is employed in analysis, education, software and communication protocol creation, and network troubleshooting.
Example: Capturing and analyzing data packets on a network, deep inspection of hundreds of protocols
-compressed.jpeg)
It's important to remain updated with the newest tools and techniques. In particular, OWASP changes its resources frequently, so it's a good idea to visit our website to get the most recent suggestions.
Here are some examples of different kinds of application security features :
Application security is a crucial aspect of software development to protect applications from various threats and security vulnerabilities.
- Authentication- when programmers incorporate security measures to guarantee that an application is only accessible by those who are permitted.
- Authorization- A user could be permitted to access and use the program after completing the authentication process.
- Encryption- Substantial data might be shielded from view or perhaps use by a cybercriminal by additional security procedures once the user has been authorized and utilizing the application
- Logging- In the event of an application security breach, logging can assist in determining who accessed the data and how.
- Application security testing- An essential procedure to guarantee the appropriate operation of each of these security features.
After talking through the basic information, it's time to learn about the most effective approaches and various types of security testing.
.webp)
Top Best Practices to Perform Security Testing
To ensure that systems and applications are resistant to potential security threats, security testing is an essential part of the software development life cycle.
Here are some best tips to perform security testing -
💻Use automated penetration testing and scanning techniques to find common security vulnerabilities.
🔄To identify specific vulnerabilities and replicate real-world attack situations, manually test the system.
🔐Verify user input to guard against injection attacks and guarantee the accuracy of the data.
📲Put multi-factor authentication and other robust authentication methods into practice.
Here learn the best practices and tools for security testing and how to utilize them as a strategy to find and close security gaps
The top security testing options to improve the code quality are listed below:
⏩SolarWinds Security Event Manager (FREE TRIAL) -A Security Information and Event Management (SIEM) system built to instantly gather and compile logs and events from your network's servers, firewalls, routers, and other devices
⏩SOOS (FREE TRIAL) -SCA and DAST systems are available on this cloud platform, which can be utilized for on-demand or continuous testing.
⏩Veracode- A cloud-based application security solution provider that offers, on a single platform, a variety of security testing tools, including DAST, SAST, IAST, SCA, and human penetration testing.
⏩Invicti - A vulnerability scanner that can be used in CI/CD pipelines for continuous testing and that can also be used to examine live Web applications.
⏩Acunetix- A versatile vulnerability scanner that functions as an automated penetration testing instrument. This system can be installed on Windows, macOS, or Linux, or it can be made available as a cloud platform.
⏩Metasploit- An effective tool for ethical hacking and penetration testing that both attackers and defenders use to simulate and initiate actual network attacks and run exploit code.
.webp)
Discover these Various Security Testing Types
Security testing is a critical aspect of ensuring the resilience of software, applications, and systems against potential security threats. Here are some key security testing types:
➡️Penetration Testing:
🟡Objective: To simulate a real-world attack to identify vulnerabilities that could be exploited.
🟡Methodology:
- Evaluate the impact of successful exploits and the overall security posture of the organization.
- Provide clear and actionable recommendations for mitigating the identified vulnerabilities and improving security.
- Create a detailed report summarizing the findings, including an executive summary for non-technical stakeholders.
🟡Focus: Identifying and fixing specific security vulnerabilities.
➡️Vulnerability Assessment:
🟡Objective: Systematic examination of the system to identify potential security vulnerabilities.
🟡Methodology:
- Automated tools are often used to scan the system for known vulnerabilities.
- Use automated tools and manual techniques to identify and assess vulnerabilities.
- Attempt to exploit identified vulnerabilities to gain unauthorized access.
🟡Focus: Identifying weaknesses that could be exploited.
➡️Security Auditing:
🟡Objective: Evaluating the security of an entire system or organization, including policies and procedures.
🟡Methodology:
- In-depth examination of security policies, configurations, and practices.
- Conduct a vulnerability assessment to identify and prioritize potential security weaknesses.
- Evaluate the security of the organization's network infrastructure, including firewalls, routers, and intrusion detection/prevention systems
🟡Focus: Ensuring compliance with security policies and best practices.
➡️Security Scanning:
🟡Objective: Identifying vulnerabilities in a system's network or infrastructure.
🟡Methodology:
- Automated tools scan the network for open ports, misconfigurations, and vulnerabilities.
- Classify assets based on their criticality and importance to the organization.
- Compile an inventory of all assets within the defined scope, including servers, network devices, and applications.
🟡Focus: Identifying and fixing network-related vulnerabilities.
➡️Code Review/Static Analysis:
🟡Objective: Analyzing the source code for security vulnerabilities without executing the program.
🟡Methodology:
- Manual or automated review of the codebase.
- Assemble a team of reviewers with diverse skills and expertise.
- Establish clear coding standards for your project, covering syntax, naming conventions, formatting, and best practices
🟡Focus: Identifying vulnerabilities in the code itself.
➡️Dynamic Analysis (Dynamic Application Security Testing - DAST):
🟡Objective: Assessing an application in a runtime environment to find security vulnerabilities.
🟡Methodology:
- Automated tools simulate attacks and identify vulnerabilities during application runtime.
- Insert code (instrumentation) into the application to collect runtime information, such as function calls, memory usage, and variable values.
- Run the instrumented application in various scenarios to simulate real-world usage.
🟡Focus: Identifying vulnerabilities that may be exploited in a live environment.
➡️Fuzz Testing:
🟡Objective: Inputting random or unexpected data to find vulnerabilities.
🟡Methodology:
- Automated tools generate random inputs to identify unexpected system behavior.
- Mutate the seed input by making random changes, such as flipping bits, changing values, or altering the structure
- Feed the mutated input to the target application.
🟡Focus: Identifying vulnerabilities related to input handling.
➡️Security Awareness Training:
🟡Objective: Educating personnel about security policies, procedures, and best practices.
🟡Methodology:
- Conduct realistic phishing simulations by sending simulated phishing emails to employees, mimicking common phishing tactics
- Provide immediate feedback to employees who fall for the simulated phishing attacks, directing them to relevant training materials and resources
🟡Focus: Building a security-aware culture within the organization.
➡️Social Engineering Testing:
🟡Objective: Assessing the effectiveness of an organization's security controls against human manipulation.
🟡Methodology:
- Simulating social engineering attacks (e.g., phishing) to test employee awareness.
- Attempt unauthorized access to secure areas, attempting to tailgate behind authorized individuals or finding unsecured entry points
- Document the effectiveness of physical security controls, such as access badges, security personnel, and surveillance systems
🟡Focus: Identifying vulnerabilities related to human behavior.
➡️Mobile Application Security Testing (Mobile AST):
🟡Objective: Assessing the security of mobile applications.
🟡Methodology:
- Combines various testing types, such as dynamic analysis, static analysis, and penetration testing.
- Examine configuration files and settings to identify misconfigurations that may lead to security vulnerabilities
- Provide a detailed report highlighting identified vulnerabilities, including their severity and recommendations for remediation.
🟡Focus: Identifying vulnerabilities specific to mobile platforms.

Choose your Security Testing Tools for Best Results.
👉 Depending on your unique requirements, the makeup of your apps, and the kinds of vulnerabilities you need to find, you can choose the finest security testing tools✅.
- Nmap (Network Mapper):
.webp)
- Metasploit:
.webp)
- Wireshark:
.webp)
- BeEF (Browser Exploitation Framework):
.webp)
- Aircrack-ng:
.webp)
- OpenVAS (Open Vulnerability Assessment System):
.webp)
Mobile App and Web App Security Testing
👉 Key Challenges in Mobile App Security Testing
➡️The term "mobile app security" describes the procedures and policies put in place to shield mobile apps and the data they manage from different security risks and weaknesses.
Mobile app security testing should include a range of topics, such as:
🟢Device Fragmentation: Applications for mobile devices must work flawlessly on a variety of devices with varying screen sizes, resolutions, and hardware setups.
🟢Operating System Diversity: Different operating systems, including iOS and Android, are used by mobile apps, and each has unique security features. Testing needs to take these variations into consideration.
➡️The following are some essential tactics to improve mobile app security:
- Secure Coding Practices:
- Train developers on secure coding practices to write robust and secure code.
- Conduct regular code reviews to identify and fix security vulnerabilities.
- Authentication and Authorizations:
- Implement strong user authentication mechanisms, such as multi-factor authentication (MFA).
- Use appropriate authorization controls to ensure users have the necessary permissions.
- Data Encryption:
- Encrypt sensitive data both in transit and at rest to protect it from unauthorized access.
- Use secure protocols (e.g., HTTPS) for communication between the app and servers.
➡️How to Perform Web Application Security Testing
- Web App Security Testing: Ensuring that the program verifies and cleans user inputs to stop typical vulnerabilities like SQL injection and XSS attacks is known as input validation.
- Authentication and Authorization: Checking the robustness of authentication systems and making sure that the right authorization rules are in place to limit access to functions that are sensitive.
- Secure File Uploads: If the program permits file uploads, testing ought to confirm that the procedure is safe from malicious uploads.
➡️ In order to guarantee the security of a web application, a comprehensive manual evaluation is required. The procedures for conducting web application security testing are as follows✅:
- Asset Discovery: Determine the crucial security points in your application. It entails identifying the different components and sources that contribute to the testing procedure.
- Version Check: Make sure the program is up to date and compliant with security standards by checking for updates. Include any related assets in this assessment as well.
- Permissions Audit: Examine the program to confirm that user roles and permissions are implemented in accordance with security requirements. It guarantees that only those with permission can access.
- Security Protocol Assessment: Look over crucial security precautions like malware scanners, firewalls, and SSL protocols. By using these technologies, the application is protected from possible risks.
- Database Security Testing: Assess the database to ensure that it is protected from malicious SQL queries, reducing the possibility of unauthorized access to the data.
- Configuration Validation: Examine the network's and the application's configuration hierarchy. To avoid any security breaches, make sure they follow the setups.
- Input Validation Testing: Verify the existence of efficient validation procedures by carefully examining user-provided data input mechanisms.
- Review of Authentication and Session Management: Examine authentication protocols and session management practices to determine how resilient they are to possible attacks.
- Configuration Check: Make sure all web application configurations are present and positioned correctly. If they are not, vulnerabilities may be revealed.
Explore Security Certification Through Comparison in greater detail
Verify experts' abilities and expertise in a range of areas related to data, network, and digital system security. Let's compare a few common security certifications:
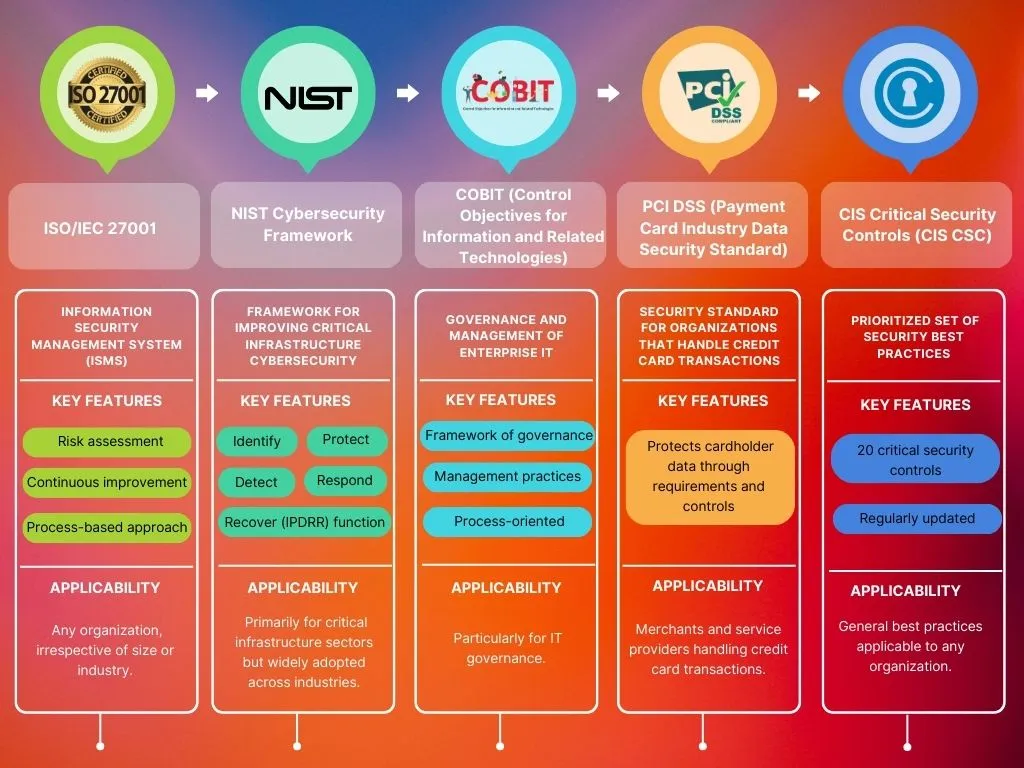
Check out more of Security Frameworks
Certainly! Security frameworks play a crucial role in ensuring the protection of information, systems, and networks. Here's a brief comparison of some popular security frameworks:
Data driven framework
👉 A data-driven framework is a testing approach that facilitates easy change and scalability by storing test input and output values in external data files.
👉Short-term advantages of putting in place a data-driven framework include the following:
⏩Efficiency: By altering external data files, you may quickly respond to changes in test cases and minimize the need for code modifications.
⏩Reusability: To maximize test development efficiency, reuse test scripts for various data sources.
⏩Scalability: Add or change data sets to easily expand test coverage without requiring significant script revisions.
⏩ Upkeep: Make maintenance easier by allowing modifications to be made externally to test cases without affecting the underlying code.
⏩Parallel Execution: To expedite the testing process overall, run tests in parallel utilizing several data sets.
Keyword Driven Framework security testing
Generally speaking, a "Keyword Driven Framework" is a test automation framework in which certain inputs or conditions direct or drive the testing process.
The following are the main features of a security testing framework that is keyword-driven.
- Keyword Repository:
- Define Keywords: Identify and define a set of keywords that represent specific security test actions, such as login, input validation, authentication, authorization, encryption, etc.
- Test Case Design:
- Test Steps Using Keywords: Design security test cases by specifying the sequence of keywords that need to be executed for each test scenario.
- Parameterization:
- Dynamic Data: Use dynamic data generation techniques within keywords to simulate different scenarios and test cases.
- Automation:
- Tool Integration: Integrate security testing tools into the keyword-driven framework, enabling the execution of specific security actions using keywords.
- Data-Driven Approach:
- Data Tables/Sheets: Utilize data tables or sheets to parameterize test data, allowing for a data-driven approach within the keyword-driven framework.
- Modularity and Maintainability:
- Easy Maintenance: Enable easy maintenance and updates by making changes to individual keywords without affecting the entire test suite.
Visual Validation framework security testing
➡️Verifying a software application's visual elements is the main goal of the testing methodology known as visual validation.
Here are some key considerations to keep in mind.
⏩Data Privacy: Ensure that any screenshots or visual representations captured during testing do not contain sensitive or personally identifiable information.
⏩Access Controls: Restrict access to the Visual Validation Framework to authorized personnel only.
⏩Secure Storage: Store visual validation data, such as screenshots or baseline images, in a secure and encrypted environment.
⏩Network Security: Ensure secure transmission of visual validation data between testing components.
⏩Integration with CI/CD Pipelines: If integrating the Visual Validation Framework into a continuous integration/continuous deployment (CI/CD) pipeline, ensure that the process is secure and doesn't introduce vulnerabilities.
⏩Regular Security Audits: Conduct regular security audits of the Visual Validation Framework to identify and address potential vulnerabilities.e some key considerations to keep in mind.
Example of Security testing Framework:
➡️ In order to find and fix security flaws in a system or application, a complete security testing framework must include a number of tools, techniques, and practices. This is an illustration of a framework for security testing that combines many components ✅.
- Test Planning and Strategy: Define the scope of security testing, including the target application, environments, and specific security requirements in the development environment.
- Requirements Analysis: Analyze security requirements and specifications to identify key security features that need testing.
- Tool Selection: Choose a set of security testing tools based on the requirements and technologies of the application.
Example tools include:
-compressed%2520(1).jpeg)
Before we move on, let's circle back to the highlights 💯
We've covered a lot of ground with our expertise in this subject, from the value of security testing to the approaches used in the modern world.
Our experience with security testing has given valuable insights into contemporary best practices and highlighted the constant need for creativity and adaptation in the rapidly evolving field of cybersecurity.
But here's a little bonus for you- a free security testing checklist for all your Security testing project. 💥
Here is one of the best and easiest ways to learn, just go through the link and explore more about security testing.
Find More Answers related to Functional Testing
Why is it important to continuously conduct penetration testing for a strong security system?
Penetration testing is a type of security assessment that examines a computer system, network, or software application to identify security flaws that an attacker could exploit.
What is pen testing in cyber security?
Penetration testing's main objective is to evaluate a system's security by trying to take advantage of its weaknesses in the same way that a malevolent attacker would.
What is QA security testing?
The process of assessing and validating a software application's security features to find vulnerabilities and make sure it can withstand potential security attacks is called QA security testing, sometimes referred to as security testing or security quality assurance.
When should security testing be done?
To guarantee that security measures are implemented properly, security testing should be a crucial component of the software development lifecycle and should be carried out at different phases in the development process.
Does Security Testing Require Coding?
Depending on the exact type of security testing being done, different levels of technical competence may be required, and coding skills may be necessary to address the common vulnerabilities.



.webp)
%201.webp)