Cybersecurity threats are everywhere, and data breaches are making big waves. It shows how essential it is to have strong defenses. That's where penetration testing comes in. This crucial process simulates real-world attacks to find vulnerabilities before hackers do.
This blog explores the differences between automated and manual penetration testing, highlighting their strengths and weaknesses. Discover why a balanced approach is vital to protecting your organization against ever-changing cyber threats.
Here is what we will cover:
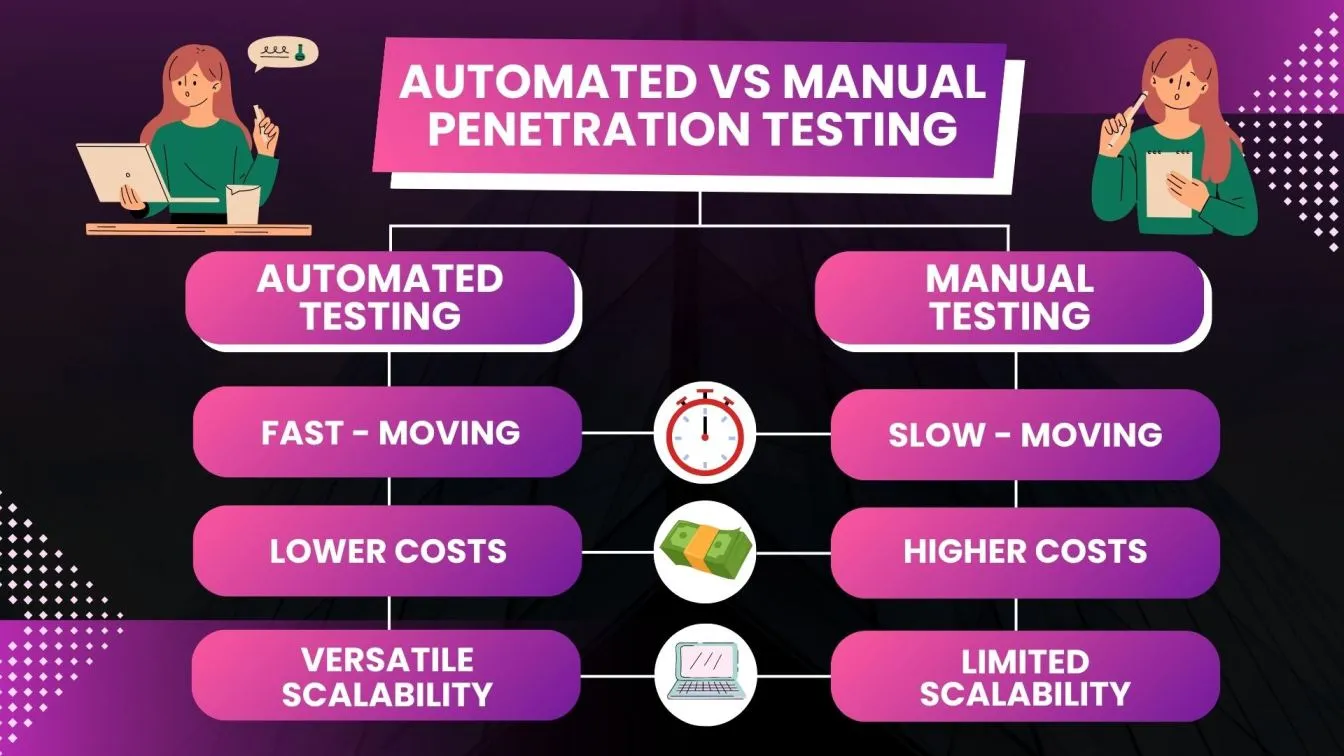
📌How to Choose Between Automated and Manual Penetration Testing: Both methods have strengths. Automated testing is faster and more cost-effective for routine checks, while manual testing offers deeper insights and human intuition to tackle complex security issues effectively.
📌Benefits of Automated Penetration Testing: Automated tools provide consistent, scalable, and rapid security assessments, minimizing human error and covering extensive ground efficiently.
📌Speed Comparison: Automated testing outpaces manual methods due to its ability to scan large systems swiftly without human intervention.
📌Cost Considerations: Automated testing generally costs less than manual testing since it requires fewer personnel hours.

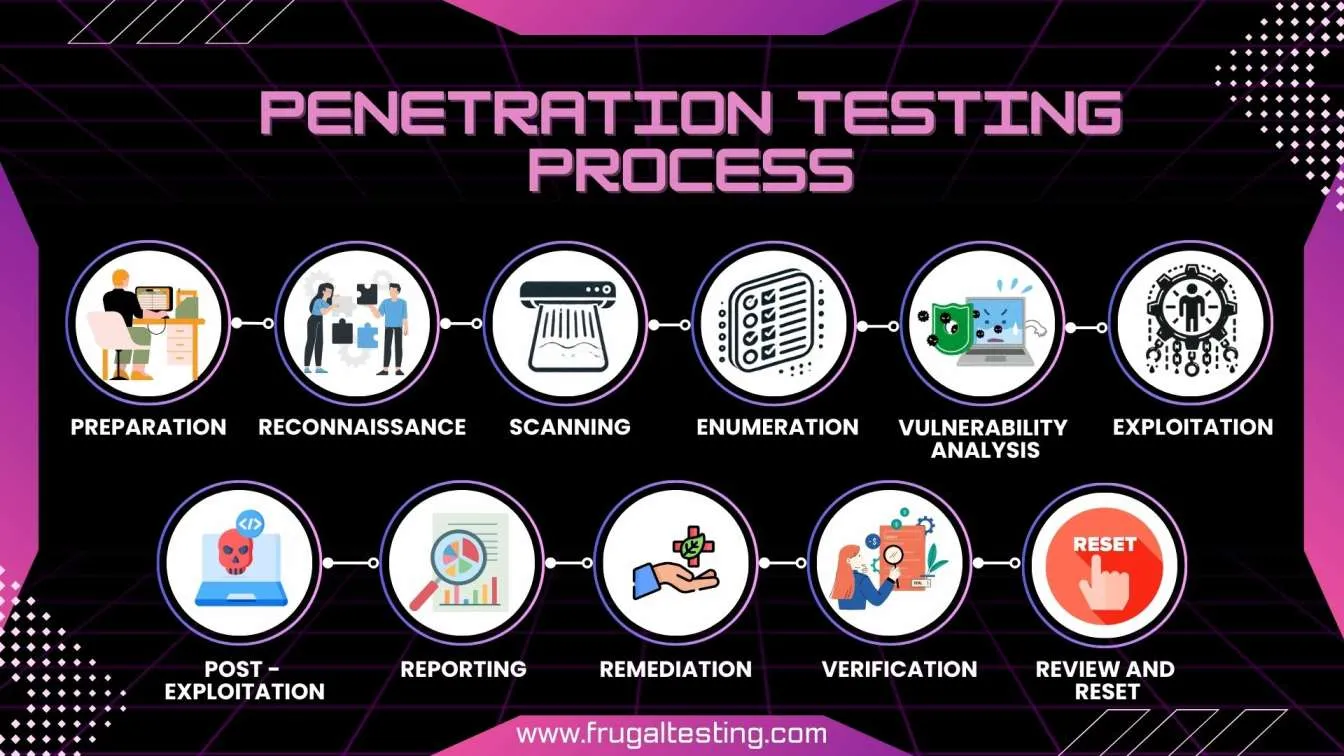
What is Penetration Testing, and Why is it important?
🔍 Penetration testing, or pen testing for short, is like having friendly hackers try to break into your computer system to find any weak spots before the bad guys do. They look for vulnerabilities in your apps, networks, and other digital areas to ensure security.
This proactive method is vital because it helps companies spot and fix security issues early on, protecting sensitive information and maintaining the trust of customers and stakeholders. In today’s world, where cyber threats are always changing, regular pen testing (include is key to keeping your systems safe and strong against potential attacks.
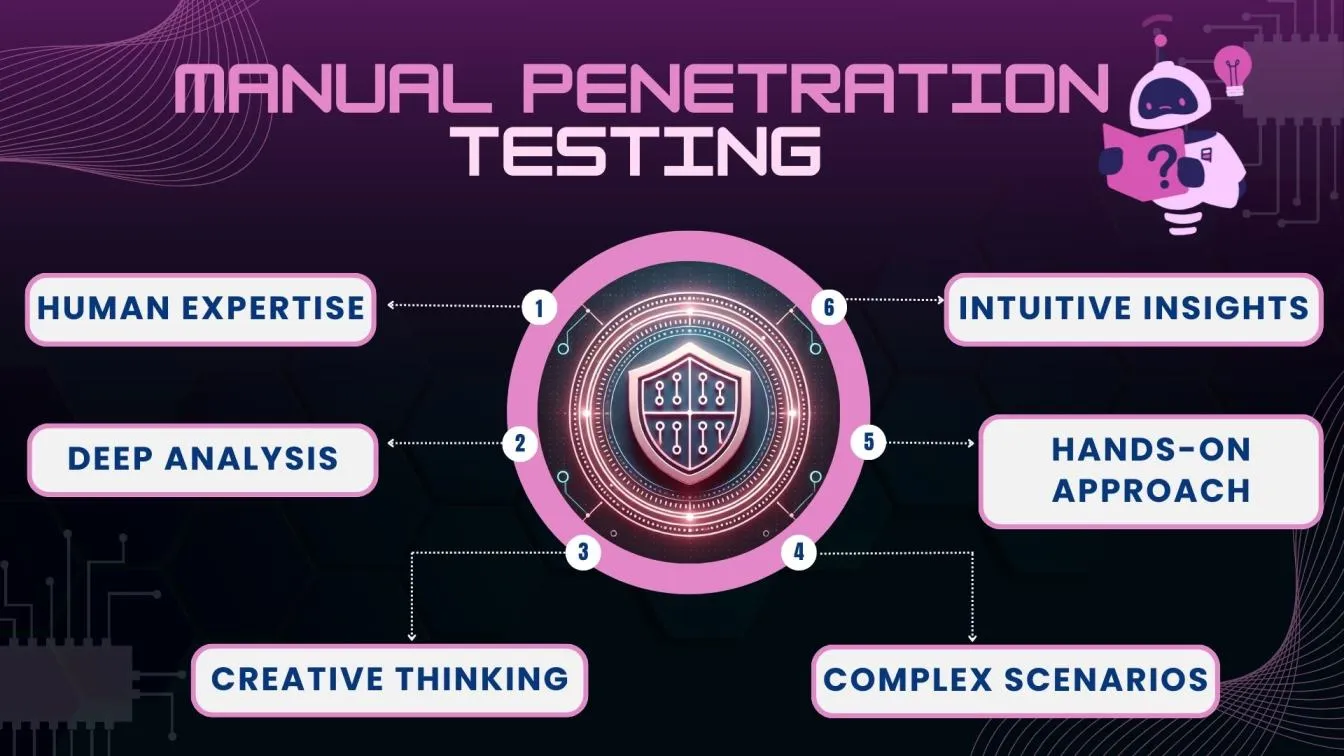
Manual Penetration Testing
🛠️Manual penetration testing is done by skilled security experts who think like hackers and use their knowledge to find weaknesses in your system. These professionals dig deep, using their intuition and experience to uncover vulnerabilities that automated tools might miss.
They can navigate complex setups and interact with applications in ways only humans can. This method is especially good for spotting logical and human-made mistakes in your system. Although it takes longer and can be costly, the detailed insights from manual testing are invaluable for securing crucial systems.
Automated Penetration Testing
🛡️Automated penetration testing (including API testing) uses software tools to scan and check systems for vulnerabilities quickly. These tools are great at covering a lot of ground fast and identifying common security issues consistently.
Automation is ideal for large-scale systems where manually checking everything is time-consuming. It’s also faster and usually cheaper than manual testing, making it perfect for regular check-ups.
However, automated testing has limits; it might miss subtle vulnerabilities that need human judgment and can’t adapt to new or complex attack methods as effectively as a human tester.

Advantages of Automated and Manual Penetration Testing
🖥️ Both automated and manual penetration testing offer unique advantages that complement each other well in securing computer systems. Here’s a comparison:
Limitations of Automated and Manual Penetration Testing
🕵️♂️ Both types of penetration testing also have their limitations, which is why a balanced approach is often recommended:

Balancing these strengths and weaknesses ensures a comprehensive approach to cybersecurity, covering a broad spectrum of potential vulnerabilities while maximizing efficiency and effectiveness in securing systems.
Examples of Manual Penetration Techniques
⚙️Manual pen-testing (which includes performance testing) involves skilled professionals using their expertise to find weaknesses in computer systems. Here are some ways they do it:
- Credential stuffing: One method is credential stuffing. Testers try using lists of usernames and passwords from other breaches to see if they can access your system's accounts. If they succeed, it shows that your security might not be strong enough to stop unauthorized access.
- SQL injection: Another way is SQL injection. Here, testers try putting harmful code into places like website search boxes. If the code works, it can give them access to parts of your database they shouldn't see or let them change information.
- Cross-site scripting (XSS): This is also common. Testers inject malicious code into web pages. If it runs when someone visits, it could steal their login information or do other harmful things, showing a vulnerability in your website's security.
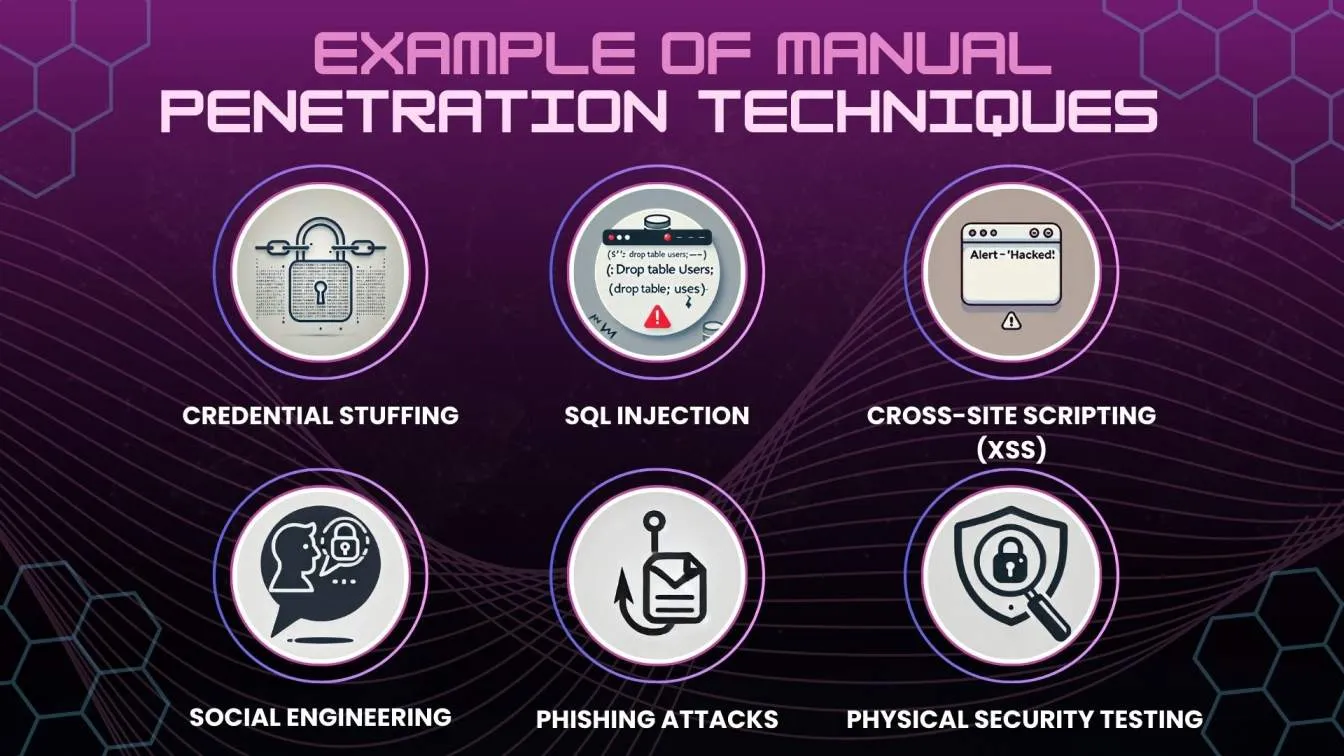
- Social engineering: This is about tricking people. Testers might pretend to be someone they're not to get sensitive information, like passwords, from your employees. This shows if your team is aware of security risks.
- Phishing attacks: These are a common tactic. Testers might send fake emails that look real, trying to get people to click on links or download attachments that could give access to your system. It shows if your team is cautious about what they click on.
- Physical security testing: Security testing involves testers trying to access sensitive areas of your office or data center physically. They might sneak in or use social tricks to get past security guards. This checks if your physical security measures are strong.
Here are some best practices:
Examples of Automated Penetration Techniques
📊Automated testing uses software to scan and test your systems for problems without needing someone to do it all by hand. Here are a few ways it works:
- Port scanning: This process is akin to inspecting a house's doors and windows to ascertain if any are unsecured. Automated tools look at all the entry points (ports) on your network to find ones that could be used by attackers to get in.
- Vulnerability scanning: This is when software checks your systems for known issues. It compares your setup to a list of problems that hackers often exploit so you can fix them before someone uses them against you.
- Password cracking: The tools try to guess passwords that are too easy or have yet to be changed from the defaults. It shows that your system needs better password security if they can get in.
- Fuzz testing: This is like throwing random things at your software to see if it breaks. Automated tools send lots of unexpected inputs to your programs to find any weak spots that could be exploited (which could also be manual tests).
- Web application scanning: This is like using a tool to automatically look for vulnerabilities in the code of your website or web application. It checks if there are ways attackers could exploit weaknesses in how your site works.
- Network sniffing: These types of tools monitor and analyze the traffic on your network. They can find sensitive information like passwords or financial data sent over the network without proper encryption, showing if your network security needs improvement.
Using these automated methods helps quickly find common problems in your security, making sure your systems are safer against cyberattacks.
Manual Penetration Testing Frameworks and Testing Guides
💡Manual penetrating testing relies on organized frameworks and guides to ensure thorough and effective security checks. Here are some commonly used ones:
Frameworks
- OWASP Testing Guide: This guide from OWASP helps testers check web applications thoroughly. It covers how applications are built and looks for problems like where hackers might sneak in or find ways to get past security (which could also be manual tests).
- PTES: The Penetration Testing Execution Standard is a step-by-step way to do penetration tests (including manual pen tests). It starts with planning and ends with finding and fixing security problems.
- CIS Critical Security Controls (CSC): This framework provides a prioritized approach to cybersecurity, focusing on critical security measures that organizations should implement. It includes guidelines for penetration testing, among other security practices.
- ISSAF: The Information Systems Security Assessment Framework is a comprehensive guide that covers various aspects of information security assessments, including penetration testing methodologies.
Testing Guides
- OSSTMM: The Open Source Security Testing Methodology Manual is a way to test security in detail. It includes testing (which could be manual tests), physical security (like how easy it is to break into a building), and checking how well operations protect systems.
- NIST SP 800-115: This guide from NIST helps with security testing. It tells how to test and fix problems in different systems, ensuring they're safe from attacks.
- PCI DSS Penetration Testing Guidance: This guide comes from the folks who set the rules for handling credit card info. It tells you exactly how to test your systems to make sure they're safe from hackers who might try to steal card details.
These guides and frameworks help penetration testers follow a clear path to finding and fixing security risks. They ensure nothing important is missed and that systems are as safe as possible from hackers. Many challenging security vulnerabilities can be uncovered when pentesters rely on their instincts and use creative methods to explore unexpected directions.
Automated Penetration Testing Frameworks and Testing Guides
🚨Automated penetration testing is like having a digital assistant that helps find and fix security holes in your systems without you having to do everything by hand. Let's break down some automated penetration testing tools that make this process smoother:
Frameworks
- Metasploit: This tool functions as a versatile multi-tool for cybersecurity. It automates scans to find vulnerabilities in networks and applications, making it easier for testers to shore up defenses before real hackers find weak spots.
- OpenVAS: Think of OpenVAS as a diligent security guard for your systems. It scans and checks for known vulnerabilities, alerting you to potential risks so you can patch them up before they're exploited.

- ZAP (OWASP Zed Attack Proxy): This tool is great for web applications. It automatically finds vulnerabilities like SQL injections or cross-site scripting by simulating attacks and pointing out where defenses might be weak.
- Dradis Framework: Dradis helps organize and manage information during penetration testing. It lets teams collaborate on findings, making tracking and fixing security issues easier.
Testing Guides
- Burp Suite: If your business has a website or web apps, Burp Suite is your go-to. It automates checks for common flaws hackers love exploiting, like weak passwords or unprotected data entry points.
- Nmap: This tool is like a detective for your network. It scans all the nooks and crannies (or ports) to see which ones are open and might let in cyber intruders, giving you a heads-up on where to tighten security.
Acunetix: It's like having an expert auditor for your web applications. Acunetix scans for security weaknesses automatically, providing detailed reports on how to fix any vulnerabilities it finds.
These frameworks and guides empower security teams to conduct automated penetration testing efficiently, ensuring that vulnerabilities are identified and mitigated promptly to enhance overall cybersecurity posture.

Final Thoughts
🚀Penetration testing, essential for securing computer systems, involves two main approaches: automated and manual pen testing. Both methods are crucial for maintaining robust cybersecurity and addressing legal considerations such as proper authorization and regulation compliance.
Automated tools provide fast, scalable assessments, are ideal for routine checks, and are cost-effective due to reduced human effort. They excel in identifying common vulnerabilities but may miss nuanced or complex security issues.
In contrast, manual pen testing, conducted by skilled experts who think like hackers, offers deeper insights into intricate scenarios and human-made errors. It ensures comprehensive security by uncovering vulnerabilities that automated pen testing tools might overlook. However, manual pen testing is more time-consuming and costly, requiring skilled labor.
A balanced approach integrating automated efficiency with manual expertise ensures thorough protection against evolving cyber threats, safeguarding sensitive data and fostering stakeholder trust.🚀

People also asked
👉 What are the benefits of Automated Penetration Testing?
Automated penetration testing offers consistent, fast, and scalable security assessments with reduced human error.
👉 Which is faster, Automated or Manual Testing?
Automated testing is faster than manual pen testing.
👉 Is Automated Testing Cheaper than Manual Testing?
Automated testing is generally cheaper than manual pen testing due to reduced labor costs.
👉 Why choose Manual Testing over Automation Testing?
Manual testing is chosen over automation for its ability to handle complex scenarios and provide human insights that automated pen testing tools might miss.
👉 What are the legal implications of Penetration Testing?
Penetration testing has legal implications, such as requiring proper authorization to avoid unauthorized access and compliance with relevant laws and regulations.




%201.webp)