Aadhaar Payment Systems (AEPS) have transformed access to banking in India by enabling secure, Aadhaar authentication and biometric authentication-based transactions even in remote areas. While this digital innovation enhances financial inclusion, it also exposes Aadhaar payments to several security risks.
From biometric spoofing to agent fraud and identity theft, the challenges are real and growing. This guide examines common Aadhaar payment vulnerabilities, real-world fraud cases, and practical measures to enhance security. Whether you're a fintech provider, banking professional, or policy strategist, understanding these threats is essential to building a safer Aadhaar-enabled ecosystem.
💡What’s Next? Keep reading to discover:
🚀 How AEPS works using an Aadhaar-based biometric authentication system.
🚀 Major security risks like fingerprint spoofing, data leaks, and agent fraud.
🚀 Real-world fraud cases showing AEPS misuse in rural banking areas.
🚀 Smart prevention methods through secure devices and user training.
🚀 How can better safeguards improve trust in Aadhaar payments?
What Are Aadhaar-Enabled Payment Systems?
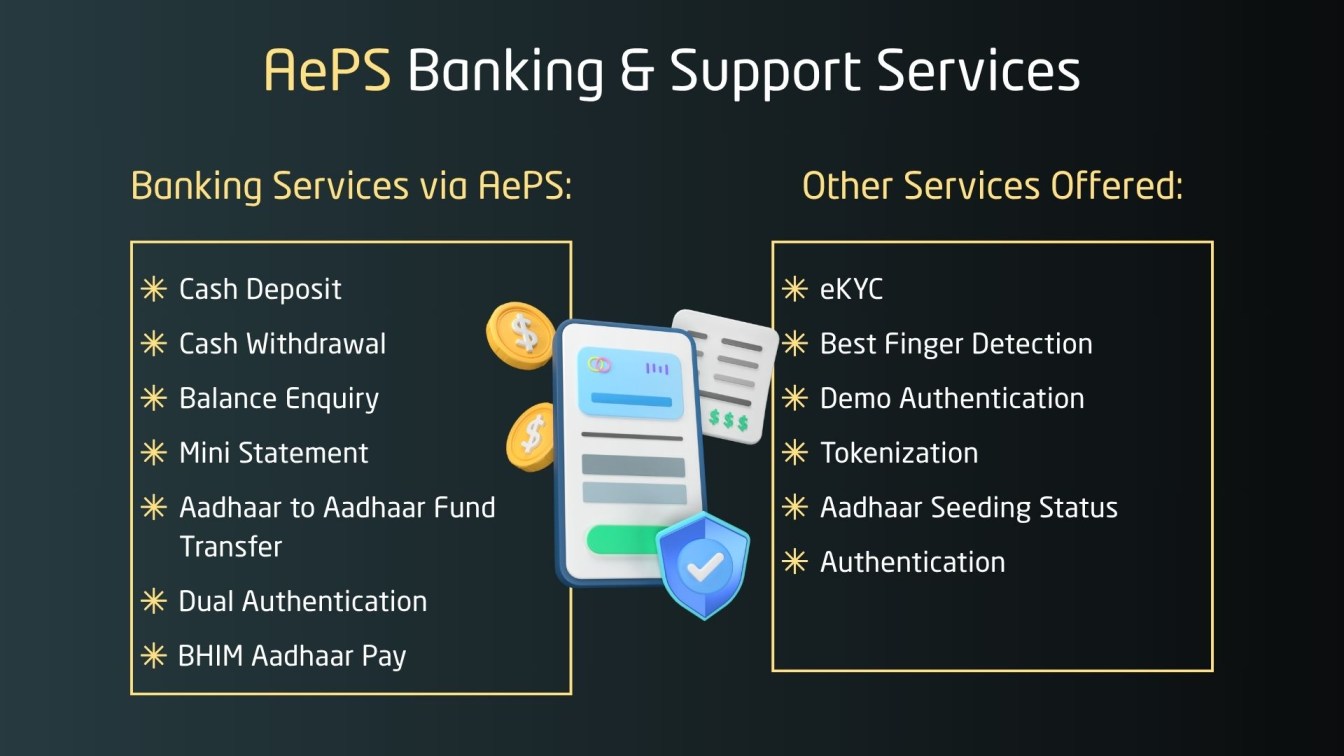
Aadhaar Enabled Payment Systems (AEPS) enable users to perform basic banking transactions, such as cash withdrawal, balance inquiry, and fund transfers, using their Aadhaar card and biometric authentication. Especially beneficial in rural areas, AEPS removes the need for debit cards or PINs.
Transactions are processed via NPCI, with OAuth authentication and Aadhaar verification handled through the UIDAI database. This ensures secure access through a reliable identity verification solution. These identity verification solutions help banks and agents ensure accurate Aadhaar linkage and reduce the chance of fraud.
AEPS uses a customer’s Aadhaar-linked bank account as the access point. By combining financial inclusion with strong verification, Aadhaar becomes a safe and effective digital payment system for underserved populations. AEPS ensures secure access through biometric identification, verifying each user through unique biological markers.
How Aadhaar-Based Payments Work
The following section explains how an Aadhaar Payment System (AEPS) transaction is processed behind the scenes. While the front-end experience for the customer is simple and quick, a complex, multi-layered biometrics identity verification system ensures secure identity verification and interbank coordination.
This architecture not only enables real-time financial inclusion but also highlights areas that must be monitored to prevent Aadhaar payment vulnerabilities and reduce security risks in Aadhaar payments.
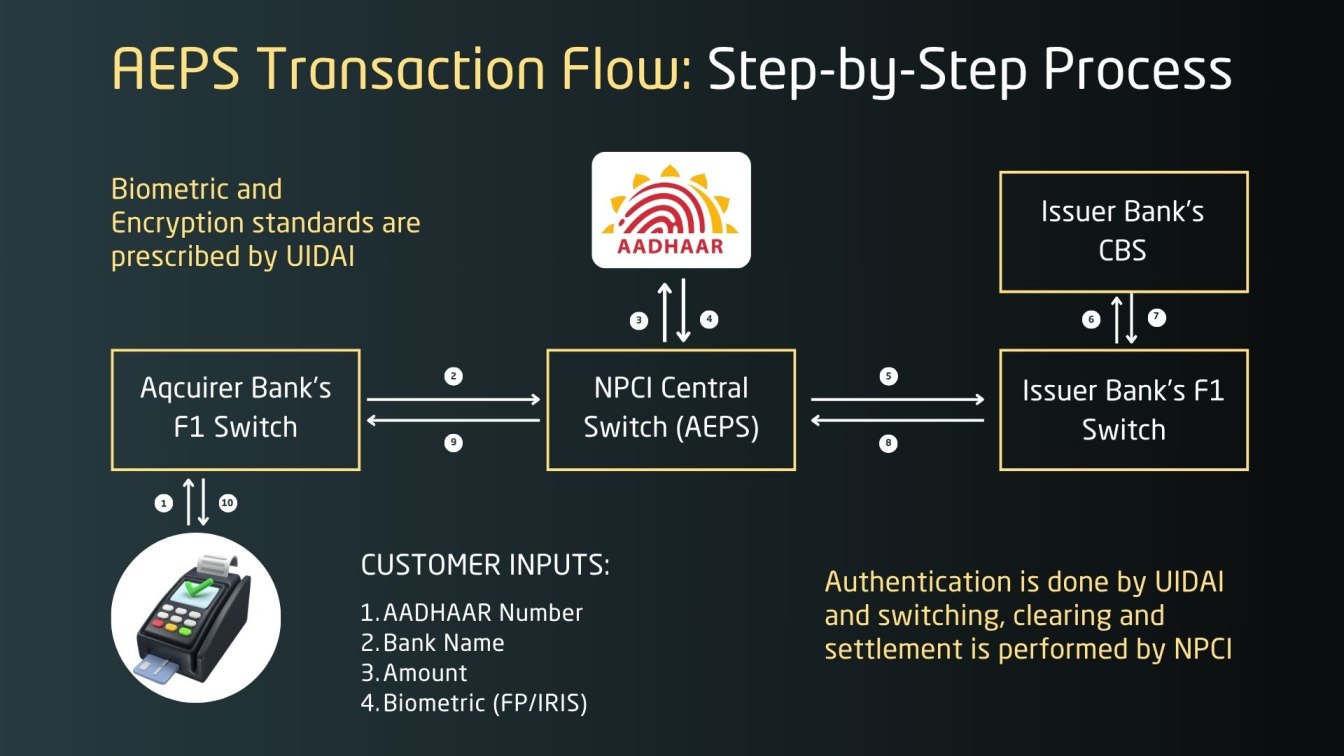
Step-by-Step Breakdown of the AEPS Flow:
- Customer Initiates Transaction
At a micro-ATM or banking agent point, the customer provides:- Aadhaar number
- Bank name
- Transaction amount
- Biometric authentication (fingerprint or iris scan)
These details are used to initiate a secure AEPS transaction.
- Request Captured by Acquirer Bank’s FI Switch
The acquiring bank’s Financial Inclusion (FI) switch receives the transaction data and prepares it for processing. - Routing Through NPCI Central Switch (AEPS)
The NPCI AEPS switch handles routing, switching, and interbank settlement. It ensures the request moves through trusted and encrypted channels. AEPS acts as a bridge between biometrics authentication and backend payment processing systems operated by banks and NPCI. - Biometric Authentication via UIDAI
UIDAI validates the fingerprint or iris scan. If identity verification fails here, the transaction is blocked, highlighting how weak biometric devices could lead to security risks in Aadhaar payments. - Forwarded to Issuer Bank’s FI Switch
Once authenticated, the transaction is sent to the customer’s bank, where the Aadhaar is linked. - Core Banking System (CBS) Validation
The issuer bank checks:- Account existence and Aadhaar linkage
- Available balance
- Potential fraud flags
It then approves or declines the transaction.
- Response Sent Back to NPCI
The result from the bank (approved/declined) is sent back to NPCI. - NPCI Sends Response to Acquirer Bank
NPCI forwards the result to the acquirer’s FI switch. - Customer Gets Confirmation
The transaction outcome is displayed to the customer at the micro-ATM, and a receipt is generated.
Types of Software Testing Used in AEPS Systems
To ensure Aadhaar Enabled Payment Systems (AEPS) are secure, efficient, and fraud-resistant, various types of software testing are implemented. These tests help verify authentication accuracy, system reliability, and user safety before deployment.
- PoC Testing:
Proof of Concept (PoC) testing by RBI and UIDAI ensures that AEPS standards like MicroATM transactions work correctly before full-scale implementation. - Security Testing:
Focuses on identifying vulnerabilities such as biometric spoofing and data theft. It includes encryption validation, penetration testing, and UIDAI-compliant security checks. - Authentication Testing:
Validates the biometric authentication process, fingerprint or iris scan, and checks two-factor authentication setups for identity verification. - Integration Testing:
Ensures seamless communication between banks, UIDAI, NPCI, and biometric devices so transactions are processed accurately and in real-time. - User Simulation Testing:
Simulates real-life transaction environments (e.g., network drops or biometric mismatches) to test user experience and system response, while also promoting user best practices for fraud prevention.
Common Security Challenges in Aadhaar Payments
AEPS growth brings security risks, especially in rural areas. Without proper testing, biometric flaws and agent misuse become common causes of data breaches and fraud.
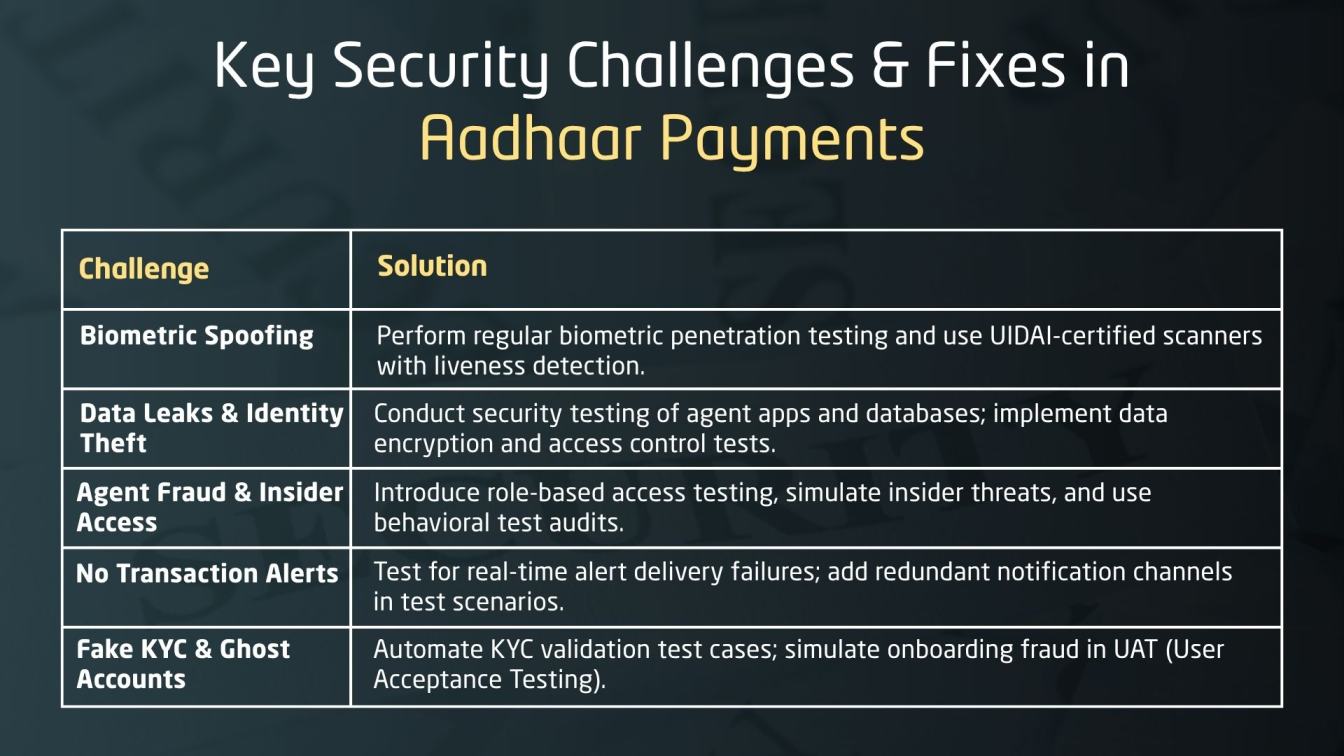
Biometric Spoofing
The first line of defense against biometric spoofing is the biometric device itself. Using certified, tamper-resistant biometric scanners ensures that common biometrics examples like fingerprints and iris scans can’t be faked or intercepted.
Why It’s a Problem:
- Fake fingerprints made from silicone or gel molds can trick basic biometric scanners.
- These biometric systems, if outdated or poorly maintained, pose a major biometric security threat by failing to detect spoofed biometrics fingerprint impressions.
- If such devices are used, even UIDAI might validate spoofed biometric data.
- Unlike passwords, biometric information cannot be changed once compromised.
- Victims may remain unaware until funds are already withdrawn from their accounts, especially if no alerts are received.
Data Leaks & Identity Theft
AEPS depends on Aadhaar-linked data like Aadhaar number, bank account, and biometric information. When this data is stored insecurely or mishandled, it can fall into the wrong hands, leading to identity theft and misuse of digital banking services.
Why It’s a Problem:
- Agents or third-party operators may store Aadhaar and bank data without proper protection, exposing users to data privacy risks.
- If a data breach happens, fraudsters can link Aadhaar numbers to bank accounts and perform fake withdrawals.
- Stolen Aadhaar identities can be used to get unauthorized loans, claim subsidies, or buy SIM cards.
- Victims often don’t realize their data is being misused until they face financial loss or benefit rejection.
- Once Aadhaar data is leaked, it is nearly impossible to revoke or change, unlike other ID systems.
- Recent data breaches involving Aadhaar have highlighted the urgent need to prevent data breaches and strengthen data security breaches protocols in digital banking systems.
Agent Fraud & Insider Access
AEPS agents, especially in rural areas, can misuse their access if strong oversight, validation, and testing are lacking.
Key Issues:
- Some agents reuse stored biometric data, bypassing secure authentication and encryption protocols.
- Weak security testing, limited compliance checks, and poor access control allow insider fraud.
- Insufficient test automation and validation of rural workflows expose system vulnerabilities.
- Lack of fraud detection testing and real-time alert systems allows suspicious activity to go unnoticed.
- Inadequate audits and low digital literacy stop users from reporting agent misuse.
No Transaction Alerts
AEPS relies on biometric authentication, but often lacks proper SMS alerts. Without real-time notifications, users may not detect fraud until it's too late.
Why It’s a Problem:
- Many users lack mobile access or live in poor network areas, so alerts are missed.
- This creates a gap in test coverage and weakens software quality assurance.
- Fraud often goes unnoticed without automated monitoring or alert systems.
- The absence of a tested offline alert mechanism reduces transparency.
- This affects trust in AEPS and the overall digital banking system.
Fake KYC and Ghost Accounts
Fraudsters take advantage of weak KYC (Know Your Customer) checks to open fake Aadhaar-linked accounts. These ghost accounts are then used to divert government funds or carry out illegal activity.
Why It’s a Problem:
- Forged documents or stolen Aadhaar numbers are used to create fake accounts during onboarding.
- These ghost accounts receive Direct Benefit Transfers (DBT) that are meant for genuine users.
- Fraudsters use fake or copied biometric impressions to keep such accounts active.
- A single Aadhaar number can be linked to multiple fraudulent accounts across banks.
- These scams are usually found only during manual audits, long after the fraud has occurred.
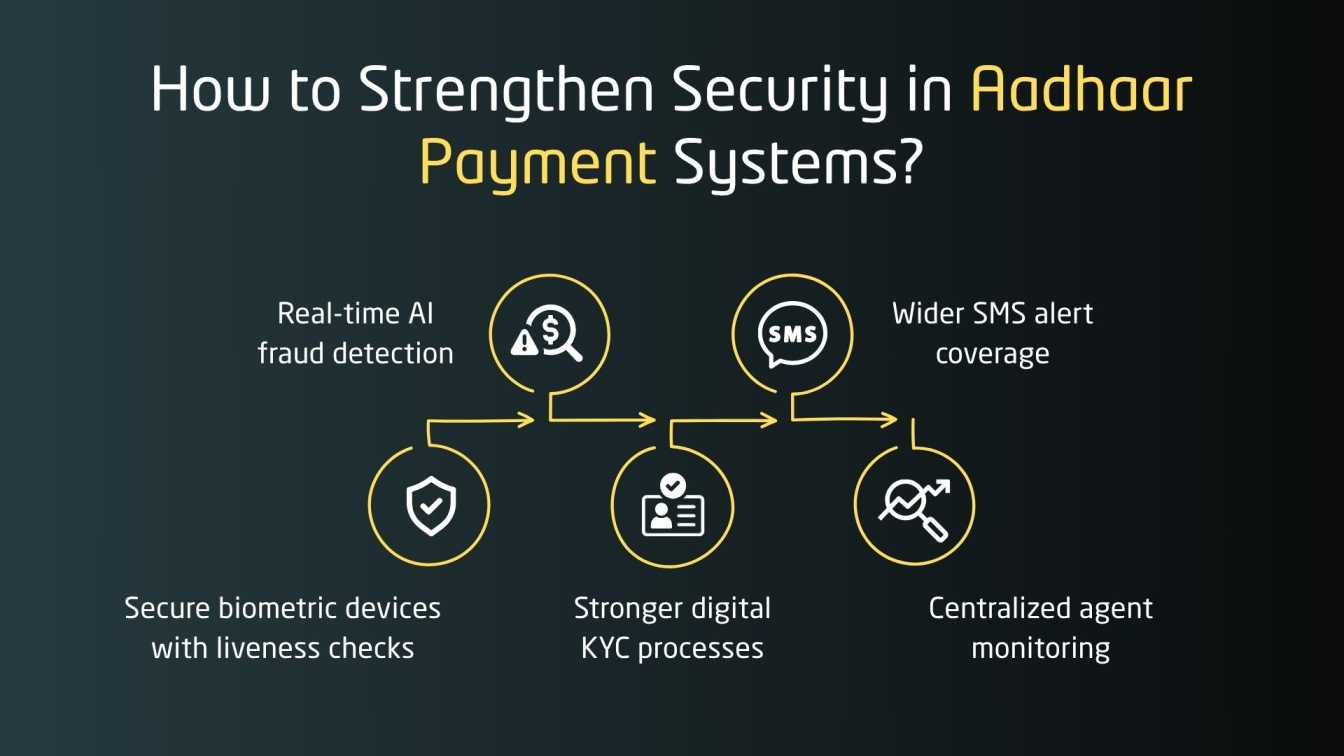
Best Ways to Prevent Aadhaar Payment Frauds
As AEPS adoption grows, preventing fraud is vital. Real-time fraud detection and strong technical controls along with user awareness are key to securing Aadhaar data and transactions.
Use of Secure Biometric Devices
The first line of defense against biometric spoofing is the biometric device itself. Using certified, tamper-resistant biometric scanners ensures that fingerprints or iris scans can’t be faked or intercepted.
Best Practices:
- Deploy only UIDAI biometric devices with encryption and liveness detection.
- Ensure devices use STQC-certified hardware and secure SDKs for capturing data.
- Avoid storing biometric data locally; ensure real-time encrypted transmission to UIDAI.
- Regularly audit devices for firmware updates and security compliance.
- Discourage use of outdated or unauthorized third-party biometric tools.
- Certified biometric technology ensures that only genuine identity verification attempts are processed, safeguarding against cloned data access.
Real-Time SMS Alerts
Sending instant SMS notifications to users after each transaction plays a critical role in fraud detection and accountability, especially in remote areas.
Best Practices:
- Ensure AEPS users have at least one Aadhaar-linked mobile number registered with the bank.
- Trigger real-time SMS alerts for every successful, failed, or attempted AEPS transaction.
- Include key details: transaction amount, time, agent location, and remaining balance.
- For areas with poor connectivity, implement offline alert alternatives such as IVR or agent-delivered slips.
Two Factor Authentication
Adding a second layer of verification can dramatically reduce unauthorized Aadhaar-based transactions, especially when biometric misuse is suspected.
Best Practices:
- Combine biometric validation with a one-time password (OTP) sent to the registered mobile number.
- Use PIN-based fallback authentication for users without SMS access.
- Implement location-based risk checks for outlier transactions (e.g., new agent, unusual time).
- Encourage banks to support adaptive authentication where the risk level determines the verification steps.
- In high-risk zones, adaptive methods such as biometric authentication paired with basic authentication or PIN fallback further minimize misuse.
Stronger Agent Verification
Agents are the backbone of AEPS delivery, but they must be held to strict compliance and monitoring standards to prevent agent fraud and insider access abuse.
Best Practices:
- Conduct background verification, biometric registration, and periodic revalidation of all field agents.
- Use agent-level transaction tracking to detect unusual patterns (e.g., repeated failed biometrics, large cash withdrawals).
- Advanced fraud detection technology helps banks track these irregularities more efficiently and flag high-risk agent behavior in real time.
- Geo-tag all AEPS agent devices for location-based monitoring.
- Suspend or blacklist agents involved in misconduct through a centralized fraud registry.
User Training and Awareness
Even with strong systems in place, the end-user remains a weak link if not informed. Awareness is critical for detecting and reporting fraud early.
Best Practices:
- Launch local-language awareness campaigns on safe Aadhaar usage.
- Educate users on never sharing Aadhaar numbers or giving biometric scans casually.
- Promote simple checks like verifying agent ID, checking receipts, and tracking bank SMSes.
- Explain the concept of basic authentication, verifying identity through straightforward methods like PINs or passwords as a backup when biometrics authentication is unavailable.
- Enable grievance redressal systems that are accessible and multilingual.
Real-World Fraud Cases and Their Impact
AEPS improves rural banking but exposes users to fraud. Real cases show how weak biometric checks and agent oversight highlight the urgent need for stronger payment testing to ensure system integrity.
1. Biometric Cloning and Fingerprint Spoofing
AEPS uses fingerprint authentication for transactions, but fraudsters have bypassed this by using fake impressions made from silicone or lifted prints. These are used at Customer Service Points (CSPs) to withdraw funds without user consent.
Example:
In Uttar Pradesh and Jharkhand, MNREGA workers and pensioners reported missing funds. Agents had cloned their fingerprints and used AEPS devices without liveness detection, enabling fraudulent withdrawals. Victims often find out only when checking balances days or weeks later.
2. Aadhaar Data Leaks and Unauthorized Access
When Aadhaar-linked information such as bank details, Aadhaar numbers, and mobile numbers is leaked, users become easy targets for identity theft and AEPS fraud.
Example: In 2018, The Tribune exposed a major leak where Aadhaar data was being sold online for just ₹500. With this data, fraudsters could access sensitive information and perform unauthorized transactions, highlighting serious data security risks in Aadhaar payments.
3. Fraudulent Withdrawals via Agent Manipulation
Some AEPS agents exploit users, especially the elderly or digitally unaware, by conducting unauthorized withdrawals and issuing fake or no receipts.
Example:
In Andhra Pradesh and Bihar, pensioners found that their accounts were debited without their knowledge. Agents reused stored biometrics or executed extra transactions during legitimate visits, taking advantage of users' limited awareness.
4. Lack of Real-Time Alerts and Transaction Visibility
Many AEPS users don’t receive SMS alerts due to unlinked mobile numbers or poor connectivity, making it difficult to detect fraud immediately.
Example:
Several Jan Dhan Yojana account holders in rural areas discovered missing funds only after visiting their bank branch. Without real-time alerts, fraudulent transactions often go unnoticed for weeks.
5. Inadequate KYC and Multiple Accounts Misuse
Weak KYC processes have allowed fraudsters to open multiple Aadhaar-linked accounts and reroute government benefit payments to fake identities.
Example:
A UIDAI audit flagged cases where LPG subsidies and other DBT transfers were sent to ghost accounts created using tampered documents and reused Aadhaar numbers. In some cases, one Aadhaar was linked to multiple fraudulent bank accounts.
Conclusion: Building a Safer Aadhaar Payment System
To secure the future of Aadhaar Payment Systems, it is vital to address risks like biometric spoofing, data breaches, and agent fraud. Using secure biometric authentication, Aadhaar verification, and real-time fraud detection solutions can help strengthen the system. Integrating advanced fraud detection software, biometric technology, and two-factor authentication will improve identity verification and reduce misuse.
As digital payment systems grow, adopting Aadhaar authentication, secure payment processing systems, and stronger KYC practices will boost trust. With better monitoring and data security safeguards, AEPS can remain a reliable and inclusive digital payment platform for millions.
Frugal Testing, a leading SaaS application testing company, is renowned for its specialized AI-driven test automation services tailored to meet the evolving needs of modern businesses. Among the comprehensive services offered by Frugal Testing are advanced Fintech Software Testing Services, designed to ensure security, performance, and compliance in financial applications. The company also provides cloud-based test automation services, enabling scalable, efficient, and cost-effective testing solutions.
People Also Ask
👉 What is the limit of Aadhaar enabled payment system?
AEPS typically allows transactions up to ₹10,000 per day per bank per Aadhaar number, but limits may vary by bank or CSP. Always check with your service provider for exact limits.
👉 Who regulates the Aadhaar enabled payment system?
AEPS is regulated by the National Payments Corporation of India (NPCI) under the guidance of the RBI and in coordination with UIDAI for Aadhaar authentication
👉 How can users protect their Aadhaar linked bank accounts?
Users should link mobile numbers to receive SMS alerts, use secure biometric devices, and avoid sharing Aadhaar or bank details with unverified agents.
👉 What is Aadhaar enabled payment system in cyber security?
In cybersecurity terms, AEPS refers to a biometric-based digital banking system vulnerable to data leaks, spoofing, and identity theft if not properly secured.
👉 What is error 300 in Aadhaar authentication failed?
Error 300 usually indicates a biometric mismatch during Aadhaar authentication, often caused by poor fingerprint quality or device-related issues.




%201.png)

.jpg)